0x00 前言
在获得对目标系统的访问权限后,但尚未提升特权的攻击者将获得什么级别的访问权限?
与其在目标系统主机上进行试验,还不如先在本地主机上了解 Windows 隐式授予非特权用户的权限。这是因为在目标主机上试验,试验过程会产生大量日志,本地测试无疑是个更好的策略选择。
在 Windows 中,几乎所有的访问都由 安全描述符 控制。这篇文章的目的是:要建立一种方法来审计由 安全描述符错误配置引起的潜在风险。
建立方法后,我们将其应用于实际用例:Windows 事件日志中授予非特权组有哪些潜在的可滥用访问?为了回答这些问题,我们应该定义以下内容:
- 什么构成配置错误?
- 什么构成“滥用”访问权限?
在回答这些问题之前,让我们首先建立获取安全描述符的方式。
Target audience:已经熟悉安全描述符、访问控制列表和 SACL 的人,都希望对其审计自动化方法进行形式化。那些不熟悉这些概念的人也可以从阅读下面 “参考” 部分中的资源得到帮助。
0x01 安全描述符
通常,安全描述符对文件、目录和注册表之类的东西提供安全保护。但是该如何识别所有的安全项目呢?对于不熟许的人来说,会认为很多事物的内核都是 “安全的”,我们称这些事物为“ 安全对象”。
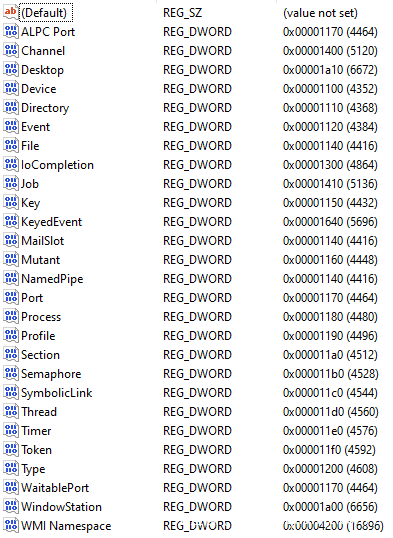
可枚举的安全对象类型的方法有几种,但我个人最先想起的方法是 James Forshaw的 NtObjectManager 项目的 PowerShell 模块中的 Get-NtType cmdlet。在没有任何参数的情况下在 Windows 10主机上运行 Get-NtType 会返回以下安全对象:
ActivationObject, ActivityReference, Adapter, ALPC Port, Callback, Composition, Controller, CoreMessaging, CoverageSampler, DebugObject, Desktop, Device, Directory, DmaAdapter, Driver, DxgkCompositionObject, DxgkCurrentDxgProcessObject, DxgkDisplayManagerObject, DxgkSharedBundleObject, DxgkSharedKeyedMutexObject, DxgkSharedProtectedSessionObject, DxgkSharedResource, DxgkSharedSwapChainObject, DxgkSharedSyncObject, EnergyTracker, EtwConsumer, EtwRegistration, EtwSessionDemuxEntry, Event, File, FilterCommunicationPort, FilterConnectionPort, IoCompletion, IoCompletionReserve, IRTimer, Job, Key, KeyedEvent, Mutant, NdisCmState, Partition, PcwObject, PowerRequest, Process, Profile, PsSiloContextNonPaged, PsSiloContextPaged, RawInputManager, RegistryTransaction, Section, Semaphore, Session, SymbolicLink, Thread, Timer, TmEn, TmRm, TmTm, TmTx, Token, TpWorkerFactory, Type, UserApcReserve, VRegConfigurationContext, WaitCompletionPacket, WindowStation, WmiGuid
但是,从返回的所有安全对象来看,似乎都与我们的特定用例无关:事件日志。 因此问题仍然存在,事件日志是否可以安全保存? 直观上讲,他们必须考虑例如无特权的用户无法查看或清除安全事件日志。
此时,最好的方法是使用 Google 搜索,搜索 “event log security descriptor” 后,以下文章浮出水面:
在本文中,它引用了通过 “CustomSD”注册表值设置自定义安全描述符的功能。它还在 “Isolation”值中设置了默认安全权限。
因此,既然我们知道安全描述符可以应用于事件日志,我们如何检索它们?
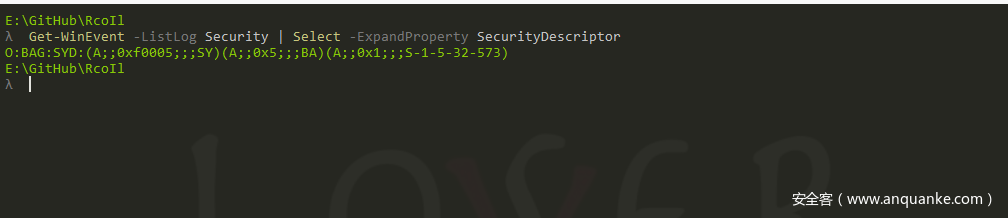
幸运的是,当在PowerShell 中调用 Get-WinEvent -ListLog 时,它将为每个事件日志返回一个EventLogConfiguration对象,其中包括 SecurityDescriptor 属性。
E:GitHubRcoIl
λ Get-WinEvent -ListLog Security | Select -ExpandProperty SecurityDescriptor
O:BAG:SYD:(A;;0xf0005;;;SY)(A;;0x5;;;BA)(A;;0x1;;;S-1-5-32-573)
作为参考,上面的字符串是 SDDL字符串,它是表示安全描述符的便捷方式。另外类似的命令 ConvertFrom-SddlString 示例为:
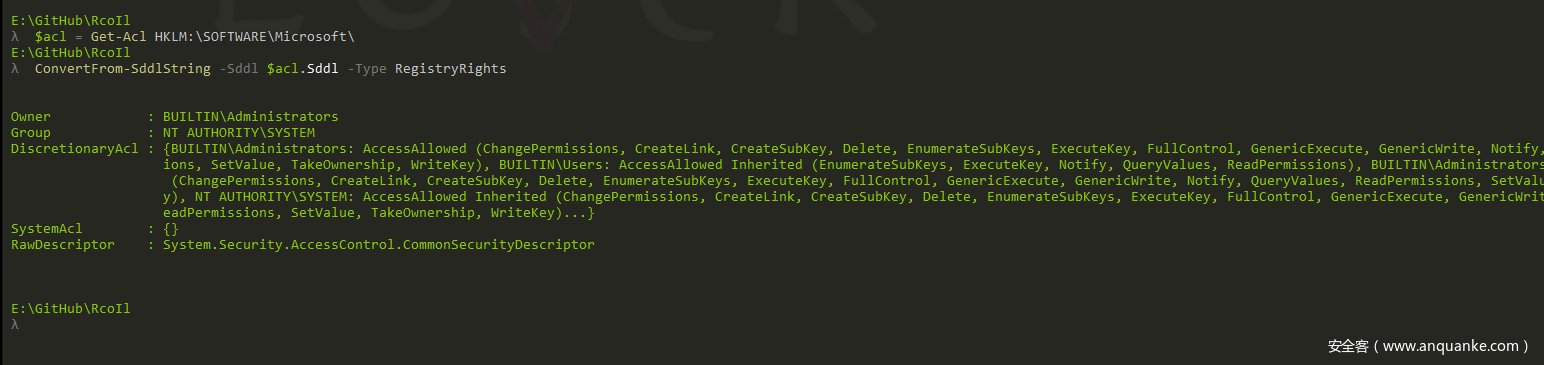
第一个命令使用Get-Acl来获取 HKLM:SOFTWAREMicrosoft 的安全描述符,并将其保存在变量中。
第二个命令使用ConvertFrom-SddlString 获取 SDDL字符串的文本表示形式,该字符串包含在表示安全描述符的对象的 Sddl 属性中。它使用-Type 参数指定 SDDL字符串 代表注册表安全描述符。
作为非常喜欢了解基础 Win32 API 的人,在使用 DnSpy 跟踪 SecurityDescriptor 属性的实现时,发现在 wevtapi.dll中调用了 EvtGetChannelConfigProperty 函数,并指定 EvtChannelConfigAccess 枚举值。
知道其中调用了相关 Win32 API 函数的 DLL 也是很有价值,因为它可以指向 Windows SDK 中的相应头文件(在本例中为 winevt.h ),该头文件通常会提供 MSDN 上未做记录的有价值的信息。
现在,如果要审核事件日志安全性描述符,我们需要知道对其应用了哪些 访问权限。
0x02 确定相关的访问权限
对于事件日志访问控制条目,我们需要弄清楚 访问掩码 的四个部分:
- 特定的对象的访问权限 – 特定的安全对象的权限,在这种情况下为事件日志;
- 标准访问权限 – 适用于安全描述符本身的权限;
- 通用访问权限 – 映射到标准和/或特定的对象的权限的权限;
- SACL访问权限 – 控制日志记录和访问的权限被授予和/或拒绝给对象。
至于特定的对象的访问权限,请参见此处。但是,有时会添加或删除访问权限,并且由于文档无法跟上更新速度。这就是为什么我更希望了解相应的Windows SDK 头文件 – winevt.h,该文件具有最新的特定的对象的访问权限定义:
#define EVT_READ_ACCESS 0x1
#define EVT_WRITE_ACCESS 0x2
#define EVT_CLEAR_ACCESS 0x4
#define EVT_ALL_ACCESS 0x7
对于那些不熟悉 bitwise operations(按位运算)的人,EVT_ALL_ACCESS 是 EVT_READ_ACCESS | EVT_WRITE_ACCESS | EVT_CLEAR_ACCESS 进行或运算的结果。
现在,映射通用访问权限会有些棘手。通用访问权限 用于映射一个或多个标准和/或特定的对象的访问权限。
对于 “鲜为人知” 的安全对象,缺少或不存在通用权限映射的说明文档,对于事件日志,也不例外。因此,在没有文档或头文件向我们提供此信息的情况下,我们就得在代码中寻找答案。
但是,我们并不知道是哪里的代码,所以我们不得不适用一些猜测和直觉来回答这个问题。我采用的方法是:使用 CustomSD 作为关键字对 DLL 进行搜索,因为此关键字与事件日志安全性实施有关,并且在 DLL 也作了对应的解释。如果能找到该关键字,那么也许与通用访问权限相关的代码可能就在关键字附近。
$EventLogAccess = ls C:WindowsSystem32*.dll | sls 'CustomSD' -Encoding unicode
$EventLogAccess.Path | Sort -Unique
得出以下结果:
C:WindowsSystem32acmigration.dll
C:WindowsSystem32aeinv.dll
C:WindowsSystem32apphelp.dll
C:WindowsSystem32appraiser.dll
C:WindowsSystem32d3d9.dll
C:WindowsSystem32drvstore.dll
C:WindowsSystem32dxdiagn.dll
C:WindowsSystem32dxgi.dll
C:WindowsSystem32generaltel.dll
C:WindowsSystem32kernel32.dll
C:WindowsSystem32opengl32.dll
C:WindowsSystem32setupapi.dll
C:WindowsSystem32vbsapi.dll
C:WindowsSystem32vfluapriv.dll
C:WindowsSystem32wevtsvc.dll
与本文最相关的 DLL 是 wevtsvc.dll,因为它是与事件日志服务关联的 DLL。
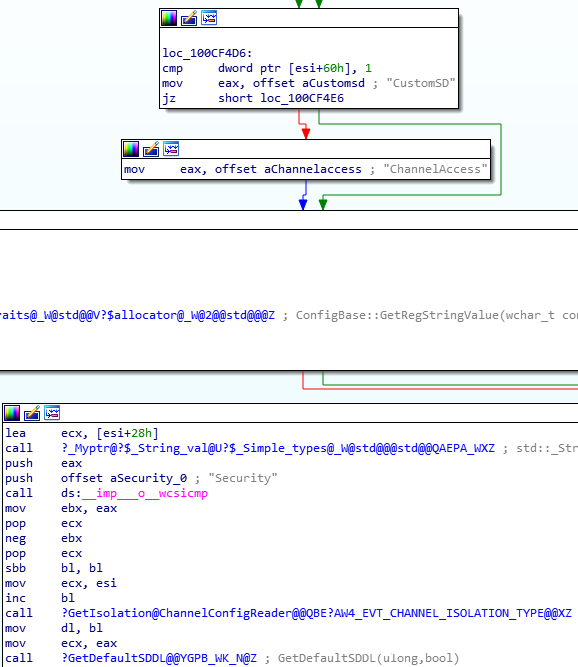
将带有符号的 wevtsvc.dll 载入 IDA 中,对 CustomSD 的交叉引用进行操作,进入 ChannelConfigReader::GetChannelAccessSddl 功能。
尽管此函数及其交叉引用没有产生任何与通用访问权限有关的内容,但 GetDefaultSDDL 函数却是非常有趣的,并且进行了最少的逆向操作后,我能看到事件日志服务在日志中定义了以下安全描述符。没有应用自定义安全描述符的情况:
- 安全日志
O:BAG:SYD:(A;;CCLCSDRCWDWO;;;SY)(A;;CCLC;;;BA)(A;;CC;;;ER)
- 系统日志
O:BAG:SYD:(A;;0xf0007;;;SY)(A;;0x7;;;BA)(A;;0x3;;;BO)(A;;0x5;;;SO)(A;;0x1;;;IU)(A;;0x3;;;SU)(A;;0x1;;;S-1-5-3)(A;;0x2;;;S-1-5-33)(A;;0x1;;;S-1-5-32-573)
- 应用日志
O:BAG:SYD:(A;;0x2;;;S-1-15-2-1)(A;;0x2;;;S-1-15-3-1024-3153509613-960666767-3724611135-2725662640-12138253-543910227-1950414635-4190290187)(A;;0xf0007;;;SY)(A;;0x7;;;BA)(A;;0x7;;;SO)(A;;0x3;;;IU)(A;;0x3;;;SU)(A;;0x3;;;S-1-5-3)(A;;0x3;;;S-1-5-33)(A;;0x1;;;S-1-5-32-573)
它们多多少少有一些对应的地方,但是与 “ Isolation” 上面的文档不同。这是另一个例子,如果你想保持准确性,就不能太依赖它的文档。既然我们有了默认事件日志安全描述符的上下文,那么在解释为什么有这么多事件日志应用相同的安全描述符时变得很重要。回到普通的访问权限,但是….
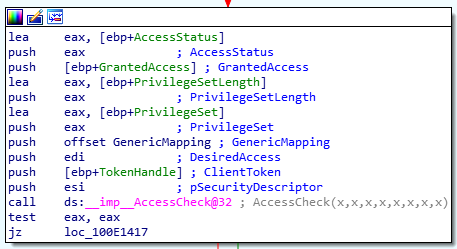
在搜寻 wevtsvc.dll 文件时,偶然发现了内部 EvtCheckAccess 函数中对 AccessCheck 函数的调用:
在看到此调用并参考相关文档之后,我可以看到此函数用于检查支持应用安全描述符的任何对象的访问。它还需要一个 GenericMapping参数。在这种情况下,wevtsvc.dll 为 AccessCheck 提供了一个由所需 GENERIC_MAPPING 结构组成的全局标量。在 IDA 中,它显示以下内容:
解释如下:
-
GENERIC_READ映射到EVT_READ_ACCESS -
GENERIC_WRITE映射到EVT_WRITE_ACCESS -
GENERIC_EXECUTE没有映射到任何特定的对象的访问权限. -
GENERIC_ALL映射到EVT_ALL_ACCESS
你可以到互联网中找到有关次文档的信息。
至此,我们现在拥有了所有必要的组件,可以对围绕审核事件日志安全描述符建立自动化。
0x03 访问权滥用注意事项
枚举目标安全对象的所有受支持的访问权限后,
你就可以开始考虑每个访问权限可能会授予无特权攻击者的个人呢利益。
经过考虑,我对每个事件日志访问权限提出了以下定义:
- EVT_READ_ACCESS:授予 用户/组 读取特定事件日志中的事件的能力。如果事件日志有可能存储敏感信息,则存在滥用的可能。此外,大多数事件日志都从任何进程的上下文中写入了事件,因此会存在由非特权用户的上下文中读取特权进程编写的事件日志的情况。
- EVT_WARTE_ACCESS:授予 用户/组 将事件写入特定时间日志的功能。使用 API 编写事件日志,这使攻击者能够生成可能给人留下良好印象的假事件日志条目。他们还可能考虑在执行记录的操作后使用良性条目填充事件日志,从而导致日志滚动并丢失其实际恶意操作的上下文。攻击者还可能选择将数据写入事件日志,以作为不会受到安全产品隔离的数据存储机制的攻击。
- EVT_CLEAR_ACCESS:授予 用户/组 清除特定事件日志的能力。非特权用户不应被授予此权利。但是,缓解性的侦查控件将是系统事件日志的事件 ID 104(来源:EventLog),该事件 ID 指示何时清除特定的事件日志。标准访问权限的含义:
- WRITE_DAC:用户/组 被授予从任意 ACL (DACL)添加/删除/修改访问控制条目的能力。事件日志中的实际含义将允许攻击者在无特权的上下文中运行,以授予它们对特定事件日志的读取/写入/清除访问权限。它们还可以删除对其他用户/组的访问权限,例如,它们将变得无法读取事件日志。
- WRITE_OWNER:授予 用户/组 获取安全描述符所有权的能力。用户/组 在那时具有完全控制权,但实际的攻击情形是为对象分配无特权的攻击者所有权,然后修改 DACL 以适合它们的需求。
这并不是要详尽列出所有已授权访问全乡的攻击者所可能所及的内容。攻击者可以滥用授予的访问权限的成都取决于以下因素:
- 攻击者可以控制的特定对象;
- 攻击者的特定目标;
- 攻击者的创造力。
0x04 安全描述符审核方法
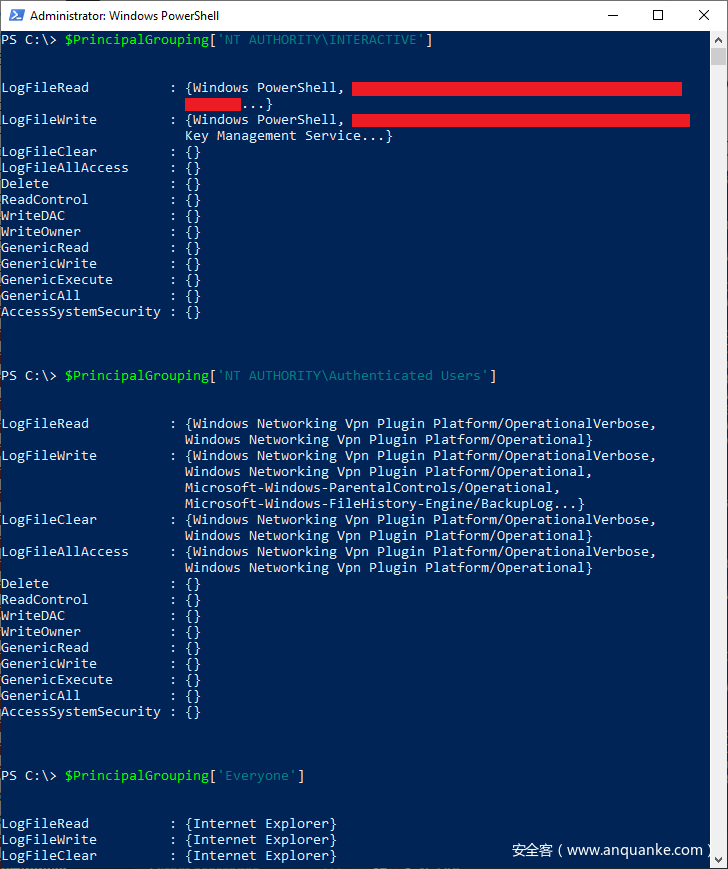
我更喜欢安全描述符审核的方式是:按允许访问的用户/组主体对访问进行分组。例如,我特别想知道 NT AUTHORITYAuthenticated Users组(非特权组)授予哪些事件日志访问权限。我编写了 powershell,以便查询内容:
# Run the following from an elevated PowerShell session
# https://gist.github.com/mattifestation/ff315b6de111fe83ded41b6df75978a8#file-eventlogauditing-ps1
# This hashtable will be used to store access rights granted to each group.
$PrincipalGrouping = @{}
# Enumerate all installed event logs
Get-WinEvent -ListLog * | ForEach-Object {
$LogName = $_.LogName
# Convert the security descriptor SDDL string to a security descriptor object.
# Doing so will facilitate reasoning over access rights.
$SecurityDescriptor = ConvertFrom-SddlString -Sddl ($_.SecurityDescriptor)
# Enumerate over every "allow" access control entry (ACE)
foreach ($ACE in ($SecurityDescriptor.RawDescriptor.DiscretionaryAcl | Where-Object { $_.AceQualifier -eq [Security.AccessControl.AceQualifier]::AccessAllowed })) {
try {
# Attempt to convert the ACE security identifier (SID) to a human-readable value
$GroupName = $ACE.SecurityIdentifier.Translate([Security.Principal.NTAccount]).Value
} catch {
# Not all SIDs can be translated. Just store the SID string if this is the case.
$GroupName = $ACE.SecurityIdentifier.Value
}
if (-not $PrincipalGrouping.ContainsKey($GroupName)) {
# If the group name has not been encountered yet, create an empty object to contain all
# the supported access rights.
$Permissions = [PSCustomObject] @{
LogFileRead = (New-Object 'Collections.ObjectModel.Collection`1[System.String]')
LogFileWrite = (New-Object 'Collections.ObjectModel.Collection`1[System.String]')
LogFileClear = (New-Object 'Collections.ObjectModel.Collection`1[System.String]')
LogFileAllAccess = (New-Object 'Collections.ObjectModel.Collection`1[System.String]')
Delete = (New-Object 'Collections.ObjectModel.Collection`1[System.String]')
ReadControl = (New-Object 'Collections.ObjectModel.Collection`1[System.String]')
WriteDAC = (New-Object 'Collections.ObjectModel.Collection`1[System.String]')
WriteOwner = (New-Object 'Collections.ObjectModel.Collection`1[System.String]')
GenericRead = (New-Object 'Collections.ObjectModel.Collection`1[System.String]')
GenericWrite = (New-Object 'Collections.ObjectModel.Collection`1[System.String]')
GenericExecute = (New-Object 'Collections.ObjectModel.Collection`1[System.String]')
GenericAll = (New-Object 'Collections.ObjectModel.Collection`1[System.String]')
AccessSystemSecurity = (New-Object 'Collections.ObjectModel.Collection`1[System.String]')
}
} else {
# The key for the specific group is already defined
$Permissions = $PrincipalGrouping[$GroupName]
}
$PrincipalGrouping[$GroupName] = $Permissions
# For each supported access right, if the group was granted access,
# add the event log name to the object.
if (($ACE.AccessMask -band 0x00000001) -eq 0x00000001) { $PrincipalGrouping[$GroupName].LogFileRead.Add($LogName) }
if (($ACE.AccessMask -band 0x00000002) -eq 0x00000002) { $PrincipalGrouping[$GroupName].LogFileWrite.Add($LogName) }
if (($ACE.AccessMask -band 0x00000004) -eq 0x00000004) { $PrincipalGrouping[$GroupName].LogFileClear.Add($LogName) }
if (($ACE.AccessMask -band 0x00000007) -eq 0x00000007) { $PrincipalGrouping[$GroupName].LogFileAllAccess.Add($LogName) }
if (($ACE.AccessMask -band 0x00010000) -eq 0x00010000) { $PrincipalGrouping[$GroupName].Delete.Add($LogName) }
if (($ACE.AccessMask -band 0x00020000) -eq 0x00020000) { $PrincipalGrouping[$GroupName].ReadControl.Add($LogName) }
if (($ACE.AccessMask -band 0x00040000) -eq 0x00040000) { $PrincipalGrouping[$GroupName].WriteDAC.Add($LogName) }
if (($ACE.AccessMask -band 0x00080000) -eq 0x00080000) { $PrincipalGrouping[$GroupName].WriteOwner.Add($LogName) }
if (($ACE.AccessMask -band 0x80000000) -eq 0x80000000) { $PrincipalGrouping[$GroupName].GenericRead.Add($LogName) }
if (($ACE.AccessMask -band 0x40000000) -eq 0x40000000) { $PrincipalGrouping[$GroupName].GenericWrite.Add($LogName) }
if (($ACE.AccessMask -band 0x20000000) -eq 0x20000000) { $PrincipalGrouping[$GroupName].GenericExecute.Add($LogName) }
if (($ACE.AccessMask -band 0x10000000) -eq 0x10000000) { $PrincipalGrouping[$GroupName].GenericAll.Add($LogName) }
if (($ACE.AccessMask -band 0x01000000) -eq 0x01000000) { $PrincipalGrouping[$GroupName].AccessSystemSecurity.Add($LogName) }
}
}
# Examples of inspecting granted permissions for unprivileged groups
$PrincipalGrouping['NT AUTHORITYINTERACTIVE']
$PrincipalGrouping['NT AUTHORITYAuthenticated Users']
$PrincipalGrouping['Everyone']
让我们看一下授予了哪些访问权限:
检查每个对象后,将向 NT AUTHORITYINTERACTIVE 组授予对最大数量的时间日志的读取和写入访问权限:
> $PGrouping['NT AUTHORITYINTERACTIVE'].LogFileRead.Count
415
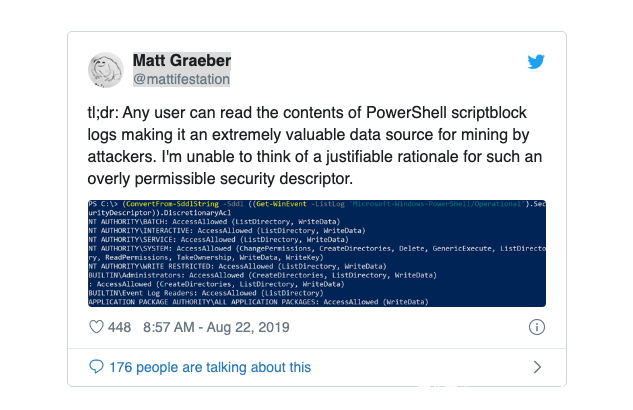
现在,从操作和研究的角度来看,你将可以确定可以确定哪些事件日志是以 NT AUTHORITYINTERACTIVE 身份运行的,这对于无特权攻击者而言特别有价值(即,任何用户都被授予了交互式登陆令牌)。例如,如果防御者正在捕获 powershell 脚本块日志,因为非特权用户具有对所有 Powershell 脚本内容的读取访问权限,包括在特权上下文中记录的内容,其中可能包括纯文本凭据,最终则让攻击者获利。
最后值得一提是是,由于可以将事件日志的自定义安全描述符用作注册表值,因此你还需要确保审核相关的注册表项的安全性,并确保无特权的用户无法将自己的自定义安全描述符写入到注册表中。
0x05 合理化默认安全描述符
尽管我尚未评估非特权用户能读取大多数事件日志的能力所带来的风险,但根据我们先前对默认安全描述符的发现,也许这至少可以阐明:为什么要向这么多日志授予访问权限。以下代码用于列出所有应用了默认 应用程序 隔离安全性的事件日志:
> $ApplicationEventLogsDefaultSDDL = 'O:BAG:SYD:(A;;0x2;;;S-1-15-2-1)(A;;0x2;;;S-1-15-3-1024-3153509613-960666767-3724611135-2725662640-12138253-543910227-1950414635-4190290187)(A;;0xf0007;;;SY)(A;;0x7;;;BA)(A;;0x7;;;SO)(A;;0x3;;;IU)(A;;0x3;;;SU)(A;;0x3;;;S-1-5-3)(A;;0x3;;;S-1-5-33)(A;;0x1;;;S-1-5-32-573)'
> Get-WinEvent -ListLog * | Where-Object { $_.SecurityDescriptor -eq $ApplicationEventLogsDefaultSDDL }
如预期那样,这几乎输出了应用程序事件日志中存在的所有事件日志。知道此信息(无论是 Microsoft 还是 Defender),将自定义的限制性更强的安全描述符应用的事件日志(如 Powershell/Operational 的日志)视为敏感的事件日志,都是好事。
0x06 安全描述符SACL研究
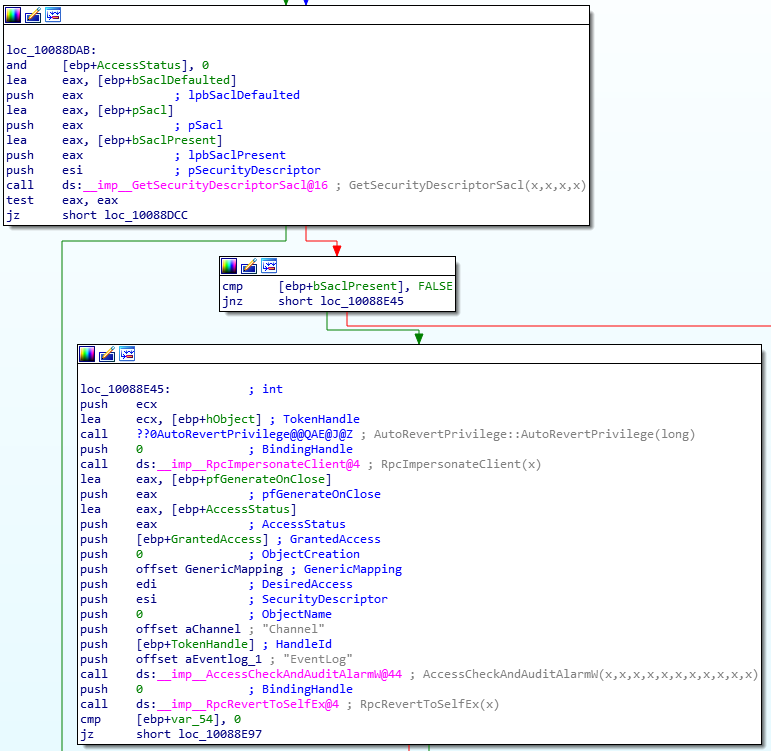
在调查事件日志安全描述符的过程中,没有可用的文档表明事件日志支持 SACL。幸运的是,内部 EvtCheckAccess 函数中存在两个相关的代码片段:GetSecurityDescriptorSacl 和 AccessCheckAndAuditAlarm
现在,知道存在用于处理 SACL 的代码,可以安全的假定它们受支持。在这一点上,我尝试将带有 SACL 的自定义安全描述符与事件日志一起应用,但不是这样做,我很想知道 Channel 自变量指的是什么。我发现它引用了一下注册表项:
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesEventLogSecuritySecurityObjectNames
因此,看起来这些都是支持 SACL日志记录的所有对象类型!! 我还确定这些 DWORD 值引用了 msobjs.dll 中的消息表索引,事件日志在记录相关 SACL 访问时从中提取消息表索引。我写了一个粗略的脚本提取这些值。
附录B 中列出所有受支持的安全对象的转储消息字符串。例如,提取了以下与Channel 对象类型相关的消息字符串:
Channel read message
Channel write message
Channel query information
Channel set information
Undefined Access (no effect) Bit 4
Undefined Access (no effect) Bit 5
Undefined Access (no effect) Bit 6
Undefined Access (no effect) Bit 7
Undefined Access (no effect) Bit 8
Undefined Access (no effect) Bit 9
Undefined Access (no effect) Bit 10
Undefined Access (no effect) Bit 11
Undefined Access (no effect) Bit 12
Undefined Access (no effect) Bit 13
Undefined Access (no effect) Bit 14
Undefined Access (no effect) Bit 15
还应该有意义的是,对于第一至第三位没有消息,因为特定的对象的访问权限仅上升了7(EVT_ALL_ACCESS),它是 111 二进制的,长度为 3 位。但是根据消息,还不清楚哪个访问权限对应于 Channel query information 还是 Channel set information。无论如何,至少现在有了这些知识,你可以了解可以记录哪些 SACL 访问权限!!
0x07 结论
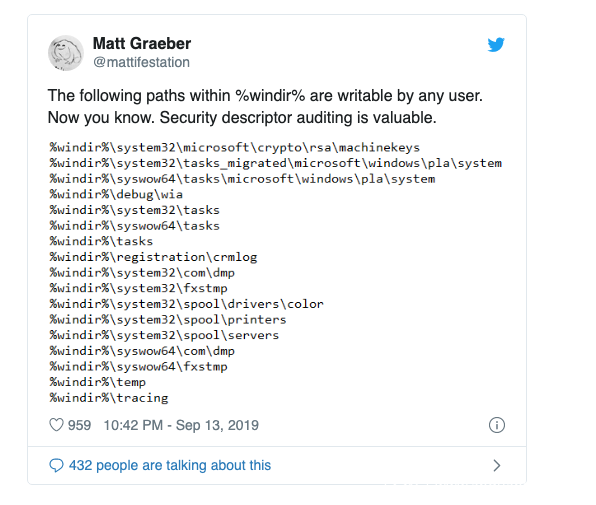
我希望本文有助于强调我用来审核的方法不仅仅是事件日志安全描述符,还包括任何可安全对象类型。该职业还应突出显示在文档不完整或不存在时进行此类型审核所涉及的挑战。
再举一个例子,我使用了这种方法来识别所有可写子目录%windir%
我还使用这种方法来理解、审计和查找 ETW 提供程序和跟踪会话中的错误配置,这在我的 Recon_2019 演讲中涉及到:
0x08 附录
8.1、附录A:NT AUTHORITYINTERACTIVE 可读可写事件日志
在撰写本文时,以下事件日志已应用了默认的 Application isolation 安全描述符,从而导致未特权的NT AUTHORITYINTERACTIVE 组成员具有读写访问权限。留给读者决定这些事件日志可能包含或可能不包含具有价值/敏感信息的成都。
授予读取访问权限:
AMSI/Operational
Application
ForwardedEvents
HardwareEvents
Key Management Service
Microsoft-AppV-Client/Admin
Microsoft-AppV-Client/Operational
Microsoft-AppV-Client/Virtual Applications
Microsoft-Client-Licensing-Platform/Admin
Microsoft-User Experience Virtualization-Agent Driver/Operational
Microsoft-User Experience Virtualization-App Agent/Operational
Microsoft-User Experience Virtualization-IPC/Operational
Microsoft-User Experience Virtualization-SQM Uploader/Operational
Microsoft-Windows-AAD/Operational
Microsoft-Windows-AllJoyn/Operational
Microsoft-Windows-All-User-Install-Agent/Admin
Microsoft-Windows-AppHost/Admin
Microsoft-Windows-AppID/Operational
Microsoft-Windows-ApplicabilityEngine/Operational
Microsoft-Windows-Application Server-Applications/Admin
Microsoft-Windows-Application Server-Applications/Operational
Microsoft-Windows-Application-Experience/Program-Compatibility-Assistant
Microsoft-Windows-Application-Experience/Program-Compatibility-Troubleshooter
Microsoft-Windows-Application-Experience/Program-Inventory
Microsoft-Windows-Application-Experience/Program-Telemetry
Microsoft-Windows-Application-Experience/Steps-Recorder
Microsoft-Windows-ApplicationResourceManagementSystem/Operational
Microsoft-Windows-AppLocker/EXE and DLL
Microsoft-Windows-AppLocker/MSI and Script
Microsoft-Windows-AppLocker/Packaged app-Deployment
Microsoft-Windows-AppLocker/Packaged app-Execution
Microsoft-Windows-AppModel-Runtime/Admin
Microsoft-Windows-AppReadiness/Admin
Microsoft-Windows-AppReadiness/Operational
Microsoft-Windows-AppXDeployment/Operational
Microsoft-Windows-AppXDeploymentServer/Operational
Microsoft-Windows-AppxPackaging/Operational
Microsoft-Windows-AssignedAccess/Admin
Microsoft-Windows-AssignedAccess/Operational
Microsoft-Windows-AssignedAccessBroker/Admin
Microsoft-Windows-AssignedAccessBroker/Operational
Microsoft-Windows-Audio/CaptureMonitor
Microsoft-Windows-Audio/GlitchDetection
Microsoft-Windows-Audio/Informational
Microsoft-Windows-Audio/Operational
Microsoft-Windows-Audio/PlaybackManager
Microsoft-Windows-Authentication User Interface/Operational
Microsoft-Windows-Authentication/AuthenticationPolicyFailures-DomainController
Microsoft-Windows-Authentication/ProtectedUser-Client
Microsoft-Windows-Authentication/ProtectedUserFailures-DomainController
Microsoft-Windows-Authentication/ProtectedUserSuccesses-DomainController
Microsoft-Windows-BackgroundTaskInfrastructure/Operational
Microsoft-Windows-BackgroundTransfer-ContentPrefetcher/Operational
Microsoft-Windows-Backup
Microsoft-Windows-Base-Filtering-Engine-Connections/Operational
Microsoft-Windows-Base-Filtering-Engine-Resource-Flows/Operational
Microsoft-Windows-Biometrics/Operational
Microsoft-Windows-BitLocker/BitLocker Management
Microsoft-Windows-BitLocker/BitLocker Operational
Microsoft-Windows-BitLocker-DrivePreparationTool/Admin
Microsoft-Windows-BitLocker-DrivePreparationTool/Operational
Microsoft-Windows-Bits-Client/Analytic
Microsoft-Windows-Bits-Client/Operational
Microsoft-Windows-Bluetooth-BthLEEnum/Operational
Microsoft-Windows-Bluetooth-BthLEPrepairing/Operational
Microsoft-Windows-Bluetooth-Bthmini/Operational
Microsoft-Windows-Bluetooth-MTPEnum/Operational
Microsoft-Windows-Bluetooth-Policy/Operational
Microsoft-Windows-BranchCache/Operational
Microsoft-Windows-BranchCacheSMB/Operational
Microsoft-Windows-CertificateServicesClient-CredentialRoaming/Operational
Microsoft-Windows-CertificateServicesClient-Lifecycle-System/Operational
Microsoft-Windows-CertificateServicesClient-Lifecycle-User/Operational
Microsoft-Windows-CertPoleEng/Operational
Microsoft-Windows-CloudStorageWizard/Operational
Microsoft-Windows-CloudStore/Debug
Microsoft-Windows-CloudStore/Operational
Microsoft-Windows-CodeIntegrity/Operational
Microsoft-Windows-Compat-Appraiser/Operational
Microsoft-Windows-Containers-BindFlt/Operational
Microsoft-Windows-Containers-Wcifs/Operational
Microsoft-Windows-Containers-Wcnfs/Operational
Microsoft-Windows-CoreApplication/Operational
Microsoft-Windows-CoreSystem-SmsRouter-Events/Operational
Microsoft-Windows-CorruptedFileRecovery-Client/Operational
Microsoft-Windows-CorruptedFileRecovery-Server/Operational
Microsoft-Windows-Crypto-DPAPI/BackUpKeySvc
Microsoft-Windows-Crypto-DPAPI/Debug
Microsoft-Windows-Crypto-DPAPI/Operational
Microsoft-Windows-DAL-Provider/Operational
Microsoft-Windows-DataIntegrityScan/Admin
Microsoft-Windows-DataIntegrityScan/CrashRecovery
Microsoft-Windows-DateTimeControlPanel/Operational
Microsoft-Windows-Deduplication/Diagnostic
Microsoft-Windows-Deduplication/Operational
Microsoft-Windows-Deduplication/Scrubbing
Microsoft-Windows-DeviceGuard/Operational
Microsoft-Windows-DeviceManagement-Enterprise-Diagnostics-Provider/Admin
Microsoft-Windows-DeviceManagement-Enterprise-Diagnostics-Provider/Operational
Microsoft-Windows-Devices-Background/Operational
Microsoft-Windows-DeviceSetupManager/Admin
Microsoft-Windows-DeviceSetupManager/Operational
Microsoft-Windows-DeviceSync/Operational
Microsoft-Windows-DeviceUpdateAgent/Operational
Microsoft-Windows-Dhcp-Client/Admin
Microsoft-Windows-Dhcp-Client/Operational
Microsoft-Windows-Dhcpv6-Client/Admin
Microsoft-Windows-Dhcpv6-Client/Operational
Microsoft-Windows-Diagnosis-DPS/Operational
Microsoft-Windows-Diagnosis-PCW/Operational
Microsoft-Windows-Diagnosis-PLA/Operational
Microsoft-Windows-Diagnosis-Scheduled/Operational
Microsoft-Windows-Diagnosis-Scripted/Admin
Microsoft-Windows-Diagnosis-Scripted/Operational
Microsoft-Windows-Diagnosis-ScriptedDiagnosticsProvider/Operational
Microsoft-Windows-Diagnostics-Networking/Operational
Microsoft-Windows-DiskDiagnostic/Operational
Microsoft-Windows-DiskDiagnosticDataCollector/Operational
Microsoft-Windows-DiskDiagnosticResolver/Operational
Microsoft-Windows-DisplayColorCalibration/Operational
Microsoft-Windows-DNS-Client/Operational
Microsoft-Windows-DriverFrameworks-UserMode/Operational
Microsoft-Windows-DSC/Admin
Microsoft-Windows-DSC/Operational
Microsoft-Windows-DxgKrnl-Admin
Microsoft-Windows-DxgKrnl-Operational
Microsoft-Windows-EapHost/Operational
Microsoft-Windows-EapMethods-RasChap/Operational
Microsoft-Windows-EapMethods-RasTls/Operational
Microsoft-Windows-EapMethods-Sim/Operational
Microsoft-Windows-EapMethods-Ttls/Operational
Microsoft-Windows-EDP-Application-Learning/Admin
Microsoft-Windows-EDP-Audit-Regular/Admin
Microsoft-Windows-EDP-Audit-TCB/Admin
Microsoft-Windows-Energy-Estimation-Engine/EventLog
Microsoft-Windows-ESE/Operational
Microsoft-Windows-EventCollector/Operational
Microsoft-Windows-Fault-Tolerant-Heap/Operational
Microsoft-Windows-FeatureConfiguration/Operational
Microsoft-Windows-FileHistory-Core/WHC
Microsoft-Windows-FMS/Operational
Microsoft-Windows-Folder Redirection/Operational
Microsoft-Windows-Forwarding/Operational
Microsoft-Windows-GenericRoaming/Admin
Microsoft-Windows-glcnd/Admin
Microsoft-Windows-HelloForBusiness/Operational
Microsoft-Windows-HomeGroup Control Panel/Operational
Microsoft-Windows-HomeGroup Listener Service/Operational
Microsoft-Windows-HomeGroup Provider Service/Operational
Microsoft-Windows-HostGuardianClient-Service/Admin
Microsoft-Windows-HostGuardianClient-Service/Operational
Microsoft-Windows-HostGuardianService-CA/Admin
Microsoft-Windows-HostGuardianService-CA/Operational
Microsoft-Windows-HostGuardianService-Client/Admin
Microsoft-Windows-HostGuardianService-Client/Operational
Microsoft-Windows-HotspotAuth/Operational
Microsoft-Windows-HttpService/Log
Microsoft-Windows-HttpService/Trace
Microsoft-Windows-Hyper-V-Guest-Drivers/Admin
Microsoft-Windows-Hyper-V-Guest-Drivers/Operational
Microsoft-Windows-Hyper-V-VMSP-Admin
Microsoft-Windows-Hyper-V-VmSwitch-Operational
Microsoft-Windows-IdCtrls/Operational
Microsoft-Windows-IKE/Operational
Microsoft-Windows-International/Operational
Microsoft-Windows-International-RegionalOptionsControlPanel/Operational
Microsoft-Windows-Iphlpsvc/Operational
Microsoft-Windows-IPxlatCfg/Operational
Microsoft-Windows-KdsSvc/Operational
Microsoft-Windows-Kerberos/Operational
Microsoft-Windows-Kernel-ApphelpCache/Operational
Microsoft-Windows-Kernel-Boot/Operational
Microsoft-Windows-Kernel-EventTracing/Admin
Microsoft-Windows-Kernel-IO/Operational
Microsoft-Windows-Kernel-PnP/Configuration
Microsoft-Windows-Kernel-Power/Thermal-Operational
Microsoft-Windows-Kernel-ShimEngine/Operational
Microsoft-Windows-Kernel-StoreMgr/Operational
Microsoft-Windows-Kernel-WDI/Operational
Microsoft-Windows-Kernel-WHEA/Errors
Microsoft-Windows-Kernel-WHEA/Operational
Microsoft-Windows-Known Folders API Service
Microsoft-Windows-LanguagePackSetup/Operational
Microsoft-Windows-LinkLayerDiscoveryProtocol/Operational
Microsoft-Windows-LSA/Operational
Microsoft-Windows-MediaFoundation-Performance/SARStreamResource
Microsoft-Windows-MemoryDiagnostics-Results/Debug
Microsoft-Windows-Mobile-Broadband-Experience-Parser-Task/Operational
Microsoft-Windows-Mobile-Broadband-Experience-SmsRouter/Admin
Microsoft-Windows-ModernDeployment-Diagnostics-Provider/Admin
Microsoft-Windows-ModernDeployment-Diagnostics-Provider/Autopilot
Microsoft-Windows-ModernDeployment-Diagnostics-Provider/ManagementService
Microsoft-Windows-Mprddm/Operational
Microsoft-Windows-MSPaint/Admin
Microsoft-Windows-MUI/Admin
Microsoft-Windows-MUI/Operational
Microsoft-Windows-Ncasvc/Operational
Microsoft-Windows-NcdAutoSetup/Operational
Microsoft-Windows-NCSI/Operational
Microsoft-Windows-NDIS/Operational
Microsoft-Windows-NdisImPlatform/Operational
Microsoft-Windows-NetworkLocationWizard/Operational
Microsoft-Windows-NetworkProfile/Operational
Microsoft-Windows-NetworkProvisioning/Operational
Microsoft-Windows-NlaSvc/Operational
Microsoft-Windows-Ntfs/Operational
Microsoft-Windows-Ntfs/WHC
Microsoft-Windows-NTLM/Operational
Microsoft-Windows-OfflineFiles/Operational
Microsoft-Windows-OneBackup/Debug
Microsoft-Windows-OneX/Operational
Microsoft-Windows-OOBE-Machine-DUI/Operational
Microsoft-Windows-OtpCredentialProvider/Operational
Microsoft-Windows-PackageStateRoaming/Operational
Microsoft-Windows-Partition/Diagnostic
Microsoft-Windows-PerceptionRuntime/Operational
Microsoft-Windows-PerceptionSensorDataService/Operational
Microsoft-Windows-PersistentMemory-Nvdimm/Operational
Microsoft-Windows-PersistentMemory-PmemDisk/Operational
Microsoft-Windows-PersistentMemory-ScmBus/Certification
Microsoft-Windows-PersistentMemory-ScmBus/Operational
Microsoft-WindowsPhone-Connectivity-WiFiConnSvc-Channel
Microsoft-Windows-Policy/Operational
Microsoft-Windows-PowerShell/Admin
Microsoft-Windows-PowerShell/Operational
Microsoft-Windows-PowerShell-DesiredStateConfiguration-FileDownloadManager/Operational
Microsoft-Windows-PrintBRM/Admin
Microsoft-Windows-PrintService/Admin
Microsoft-Windows-PrintService/Operational
Microsoft-Windows-PriResources-Deployment/Operational
Microsoft-Windows-Program-Compatibility-Assistant/Analytic
Microsoft-Windows-Program-Compatibility-Assistant/CompatAfterUpgrade
Microsoft-Windows-Provisioning-Diagnostics-Provider/Admin
Microsoft-Windows-Provisioning-Diagnostics-Provider/AutoPilot
Microsoft-Windows-Provisioning-Diagnostics-Provider/ManagementService
Microsoft-Windows-Proximity-Common/Diagnostic
Microsoft-Windows-PushNotification-Platform/Admin
Microsoft-Windows-PushNotification-Platform/Operational
Microsoft-Windows-RasAgileVpn/Operational
Microsoft-Windows-ReadyBoost/Operational
Microsoft-Windows-ReadyBoostDriver/Operational
Microsoft-Windows-ReFS/Operational
Microsoft-Windows-Regsvr32/Operational
Microsoft-Windows-RemoteApp and Desktop Connections/Admin
Microsoft-Windows-RemoteApp and Desktop Connections/Operational
Microsoft-Windows-RemoteAssistance/Admin
Microsoft-Windows-RemoteAssistance/Operational
Microsoft-Windows-RemoteDesktopServices-RdpCoreTS/Admin
Microsoft-Windows-RemoteDesktopServices-RdpCoreTS/Operational
Microsoft-Windows-RemoteDesktopServices-RemoteFX-Manager/Admin
Microsoft-Windows-RemoteDesktopServices-RemoteFX-Manager/Operational
Microsoft-Windows-RemoteDesktopServices-RemoteFX-Synth3dvsc/Admin
Microsoft-Windows-RemoteDesktopServices-RemoteFX-Synth3dvsp/Admin
Microsoft-Windows-RemoteDesktopServices-SessionServices/Operational
Microsoft-Windows-Remotefs-Rdbss/Operational
Microsoft-Windows-Resource-Exhaustion-Detector/Operational
Microsoft-Windows-Resource-Exhaustion-Resolver/Operational
Microsoft-Windows-RestartManager/Operational
Microsoft-Windows-RetailDemo/Admin
Microsoft-Windows-RetailDemo/Operational
Microsoft-Windows-RRAS/Operational
Microsoft-Windows-SearchUI/Operational
Microsoft-Windows-SecureAssessment/Operational
Microsoft-Windows-Security-Adminless/Operational
Microsoft-Windows-Security-Audit-Configuration-Client/Operational
Microsoft-Windows-Security-EnterpriseData-FileRevocationManager/Operational
Microsoft-Windows-Security-ExchangeActiveSyncProvisioning/Operational
Microsoft-Windows-Security-IdentityListener/Operational
Microsoft-Windows-Security-LessPrivilegedAppContainer/Operational
Microsoft-Windows-Security-Mitigations/KernelMode
Microsoft-Windows-Security-Mitigations/UserMode
Microsoft-Windows-SecurityMitigationsBroker/Admin
Microsoft-Windows-SecurityMitigationsBroker/Operational
Microsoft-Windows-Security-Netlogon/Operational
Microsoft-Windows-Security-SPP-UX-GenuineCenter-Logging/Operational
Microsoft-Windows-Security-SPP-UX-Notifications/ActionCenter
Microsoft-Windows-Security-UserConsentVerifier/Audit
Microsoft-Windows-SENSE/Operational
Microsoft-Windows-SenseIR/Operational
Microsoft-Windows-ServiceReportingApi/Debug
Microsoft-Windows-SettingSync/Debug
Microsoft-Windows-SettingSync/Operational
Microsoft-Windows-SettingSync-Azure/Debug
Microsoft-Windows-SettingSync-Azure/Operational
Microsoft-Windows-SettingSync-OneDrive/Debug
Microsoft-Windows-SettingSync-OneDrive/Operational
Microsoft-Windows-ShellCommon-StartLayoutPopulation/Operational
Microsoft-Windows-Shell-ConnectedAccountState/ActionCenter
Microsoft-Windows-Shell-Core/ActionCenter
Microsoft-Windows-Shell-Core/AppDefaults
Microsoft-Windows-Shell-Core/LogonTasksChannel
Microsoft-Windows-Shell-Core/Operational
Microsoft-Windows-SmartCard-Audit/Authentication
Microsoft-Windows-SmartCard-DeviceEnum/Operational
Microsoft-Windows-SmartCard-TPM-VCard-Module/Admin
Microsoft-Windows-SmartCard-TPM-VCard-Module/Operational
Microsoft-Windows-SmartScreen/Debug
Microsoft-Windows-SMBDirect/Admin
Microsoft-Windows-SMBWitnessClient/Admin
Microsoft-Windows-SMBWitnessClient/Informational
Microsoft-Windows-StateRepository/Operational
Microsoft-Windows-Storage-ATAPort/Admin
Microsoft-Windows-Storage-ATAPort/Operational
Microsoft-Windows-Storage-ClassPnP/Admin
Microsoft-Windows-Storage-ClassPnP/Operational
Microsoft-Windows-Storage-Disk/Admin
Microsoft-Windows-Storage-Disk/Operational
Microsoft-Windows-StorageManagement/Operational
Microsoft-Windows-StorageSpaces-Driver/Diagnostic
Microsoft-Windows-StorageSpaces-Driver/Operational
Microsoft-Windows-StorageSpaces-ManagementAgent/WHC
Microsoft-Windows-StorageSpaces-SpaceManager/Diagnostic
Microsoft-Windows-StorageSpaces-SpaceManager/Operational
Microsoft-Windows-Storage-Storport/Admin
Microsoft-Windows-Storage-Storport/Health
Microsoft-Windows-Storage-Storport/Operational
Microsoft-Windows-Storage-Tiering/Admin
Microsoft-Windows-Store/Operational
Microsoft-Windows-Storsvc/Diagnostic
Microsoft-Windows-SystemSettingsThreshold/Operational
Microsoft-Windows-TaskScheduler/Maintenance
Microsoft-Windows-TaskScheduler/Operational
Microsoft-Windows-TCPIP/Operational
Microsoft-Windows-TerminalServices-ClientUSBDevices/Admin
Microsoft-Windows-TerminalServices-ClientUSBDevices/Operational
Microsoft-Windows-TerminalServices-LocalSessionManager/Admin
Microsoft-Windows-TerminalServices-LocalSessionManager/Operational
Microsoft-Windows-TerminalServices-PnPDevices/Admin
Microsoft-Windows-TerminalServices-PnPDevices/Operational
Microsoft-Windows-TerminalServices-Printers/Admin
Microsoft-Windows-TerminalServices-Printers/Operational
Microsoft-Windows-TerminalServices-RDPClient/Operational
Microsoft-Windows-TerminalServices-RemoteConnectionManager/Admin
Microsoft-Windows-TerminalServices-RemoteConnectionManager/Operational
Microsoft-Windows-TerminalServices-ServerUSBDevices/Admin
Microsoft-Windows-TerminalServices-ServerUSBDevices/Operational
Microsoft-Windows-Time-Service/Operational
Microsoft-Windows-Time-Service-PTP-Provider/PTP-Operational
Microsoft-Windows-Troubleshooting-Recommended/Admin
Microsoft-Windows-Troubleshooting-Recommended/Operational
Microsoft-Windows-TWinUI/Operational
Microsoft-Windows-TZSync/Operational
Microsoft-Windows-TZUtil/Operational
Microsoft-Windows-UAC/Operational
Microsoft-Windows-UniversalTelemetryClient/Operational
Microsoft-Windows-User Control Panel/Operational
Microsoft-Windows-User Device Registration/Admin
Microsoft-Windows-User Profile Service/Operational
Microsoft-Windows-User-Loader/Operational
Microsoft-Windows-UserPnp/ActionCenter
Microsoft-Windows-UserPnp/DeviceInstall
Microsoft-Windows-VDRVROOT/Operational
Microsoft-Windows-VerifyHardwareSecurity/Admin
Microsoft-Windows-VerifyHardwareSecurity/Operational
Microsoft-Windows-VHDMP-Operational
Microsoft-Windows-Volume/Diagnostic
Microsoft-Windows-VolumeSnapshot-Driver/Operational
Microsoft-Windows-VPN/Operational
Microsoft-Windows-VPN-Client/Operational
Microsoft-Windows-Wcmsvc/Operational
Microsoft-Windows-WDAG-PolicyEvaluator-CSP/Operational
Microsoft-Windows-WDAG-PolicyEvaluator-GP/Operational
Microsoft-Windows-WDAG-Service/Operational
Microsoft-Windows-WebAuth/Operational
Microsoft-Windows-WebAuthN/Operational
Microsoft-Windows-WebIO-NDF/Diagnostic
Microsoft-Windows-WEPHOSTSVC/Operational
Microsoft-Windows-WER-PayloadHealth/Operational
Microsoft-Windows-WFP/Operational
Microsoft-Windows-Win32k/Operational
Microsoft-Windows-Windows Defender/Operational
Microsoft-Windows-Windows Defender/WHC
Microsoft-Windows-Windows Firewall With Advanced Security/Firewall
Microsoft-Windows-Windows Firewall With Advanced Security/FirewallDiagnostics
Microsoft-Windows-Windows Firewall With Advanced Security/FirewallVerbose
Microsoft-Windows-WindowsBackup/ActionCenter
Microsoft-Windows-WindowsColorSystem/Operational
Microsoft-Windows-WindowsSystemAssessmentTool/Operational
Microsoft-Windows-WindowsUIImmersive/Operational
Microsoft-Windows-WindowsUpdateClient/Operational
Microsoft-Windows-WinHTTP-NDF/Diagnostic
Microsoft-Windows-WinINet-Capture/Analytic
Microsoft-Windows-WinINet-Config/ProxyConfigChanged
Microsoft-Windows-Winlogon/Operational
Microsoft-Windows-WinNat/Oper
Microsoft-Windows-WinRM/Operational
Microsoft-Windows-Winsock-AFD/Operational
Microsoft-Windows-Winsock-NameResolution/Operational
Microsoft-Windows-Winsock-WS2HELP/Operational
Microsoft-Windows-Wired-AutoConfig/Operational
Microsoft-Windows-WLAN-AutoConfig/Operational
Microsoft-Windows-WMI-Activity/Operational
Microsoft-Windows-WMPNSS-Service/Operational
Microsoft-Windows-Wordpad/Admin
Microsoft-Windows-WorkFolders/Operational
Microsoft-Windows-WorkFolders/WHC
Microsoft-Windows-Workplace Join/Admin
Microsoft-Windows-WPD-ClassInstaller/Operational
Microsoft-Windows-WPD-CompositeClassDriver/Operational
Microsoft-Windows-WPD-MTPClassDriver/Operational
Microsoft-Windows-WWAN-SVC-Events/Operational
OpenSSH/Admin
OpenSSH/Operational
RemoteDesktopServices-RemoteFX-SessionLicensing-Admin
RemoteDesktopServices-RemoteFX-SessionLicensing-Operational
Setup
SMSApi
System
Windows PowerShell
授予写访问权限:
AMSI/Operational
Application
ForwardedEvents
HardwareEvents
Key Management Service
Microsoft-AppV-Client/Virtual Applications
Microsoft-Client-Licensing-Platform/Admin
Microsoft-User Experience Virtualization-App Agent/Operational
Microsoft-User Experience Virtualization-IPC/Operational
Microsoft-User Experience Virtualization-SQM Uploader/Operational
Microsoft-Windows-AAD/Operational
Microsoft-Windows-AllJoyn/Operational
Microsoft-Windows-All-User-Install-Agent/Admin
Microsoft-Windows-AppHost/Admin
Microsoft-Windows-ApplicabilityEngine/Operational
Microsoft-Windows-Application Server-Applications/Admin
Microsoft-Windows-Application Server-Applications/Operational
Microsoft-Windows-Application-Experience/Program-Compatibility-Assistant
Microsoft-Windows-Application-Experience/Program-Compatibility-Troubleshooter
Microsoft-Windows-Application-Experience/Program-Inventory
Microsoft-Windows-Application-Experience/Program-Telemetry
Microsoft-Windows-Application-Experience/Steps-Recorder
Microsoft-Windows-ApplicationResourceManagementSystem/Operational
Microsoft-Windows-AppLocker/MSI and Script
Microsoft-Windows-AppLocker/Packaged app-Deployment
Microsoft-Windows-AppModel-Runtime/Admin
Microsoft-Windows-AppReadiness/Admin
Microsoft-Windows-AppReadiness/Operational
Microsoft-Windows-AppXDeployment/Operational
Microsoft-Windows-AppXDeploymentServer/Operational
Microsoft-Windows-AppxPackaging/Operational
Microsoft-Windows-AssignedAccess/Admin
Microsoft-Windows-AssignedAccess/Operational
Microsoft-Windows-AssignedAccessBroker/Admin
Microsoft-Windows-AssignedAccessBroker/Operational
Microsoft-Windows-Audio/PlaybackManager
Microsoft-Windows-Authentication User Interface/Operational
Microsoft-Windows-BackgroundTaskInfrastructure/Operational
Microsoft-Windows-BackgroundTransfer-ContentPrefetcher/Operational
Microsoft-Windows-Base-Filtering-Engine-Connections/Operational
Microsoft-Windows-BitLocker/BitLocker Management
Microsoft-Windows-BitLocker/BitLocker Operational
Microsoft-Windows-Bits-Client/Analytic
Microsoft-Windows-BranchCache/Operational
Microsoft-Windows-BranchCacheSMB/Operational
Microsoft-Windows-CertificateServicesClient-CredentialRoaming/Operational
Microsoft-Windows-CertificateServicesClient-Lifecycle-User/Operational
Microsoft-Windows-CertPoleEng/Operational
Microsoft-Windows-CloudStorageWizard/Operational
Microsoft-Windows-CloudStore/Debug
Microsoft-Windows-CloudStore/Operational
Microsoft-Windows-Compat-Appraiser/Operational
Microsoft-Windows-CoreApplication/Operational
Microsoft-Windows-CoreSystem-SmsRouter-Events/Operational
Microsoft-Windows-CorruptedFileRecovery-Client/Operational
Microsoft-Windows-DAL-Provider/Operational
Microsoft-Windows-DataIntegrityScan/Admin
Microsoft-Windows-DataIntegrityScan/CrashRecovery
Microsoft-Windows-DateTimeControlPanel/Operational
Microsoft-Windows-DeviceManagement-Enterprise-Diagnostics-Provider/Admin
Microsoft-Windows-DeviceManagement-Enterprise-Diagnostics-Provider/Operational
Microsoft-Windows-Devices-Background/Operational
Microsoft-Windows-DeviceSync/Operational
Microsoft-Windows-Dhcp-Client/Admin
Microsoft-Windows-Dhcp-Client/Operational
Microsoft-Windows-Dhcpv6-Client/Admin
Microsoft-Windows-Dhcpv6-Client/Operational
Microsoft-Windows-Diagnosis-PCW/Operational
Microsoft-Windows-Diagnosis-PLA/Operational
Microsoft-Windows-Diagnosis-Scheduled/Operational
Microsoft-Windows-Diagnosis-Scripted/Admin
Microsoft-Windows-Diagnosis-Scripted/Operational
Microsoft-Windows-Diagnosis-ScriptedDiagnosticsProvider/Operational
Microsoft-Windows-Diagnostics-Networking/Operational
Microsoft-Windows-DiskDiagnosticResolver/Operational
Microsoft-Windows-DisplayColorCalibration/Operational
Microsoft-Windows-DNS-Client/Operational
Microsoft-Windows-DSC/Admin
Microsoft-Windows-DSC/Operational
Microsoft-Windows-EapHost/Operational
Microsoft-Windows-EapMethods-RasChap/Operational
Microsoft-Windows-EapMethods-RasTls/Operational
Microsoft-Windows-EapMethods-Sim/Operational
Microsoft-Windows-EapMethods-Ttls/Operational
Microsoft-Windows-EDP-Application-Learning/Admin
Microsoft-Windows-EDP-Audit-Regular/Admin
Microsoft-Windows-EDP-Audit-TCB/Admin
Microsoft-Windows-Energy-Estimation-Engine/EventLog
Microsoft-Windows-ESE/Operational
Microsoft-Windows-FeatureConfiguration/Operational
Microsoft-Windows-FileHistory-Core/WHC
Microsoft-Windows-Folder Redirection/Operational
Microsoft-Windows-Forwarding/Operational
Microsoft-Windows-GenericRoaming/Admin
Microsoft-Windows-glcnd/Admin
Microsoft-Windows-HelloForBusiness/Operational
Microsoft-Windows-HomeGroup Control Panel/Operational
Microsoft-Windows-HomeGroup Listener Service/Operational
Microsoft-Windows-HomeGroup Provider Service/Operational
Microsoft-Windows-HostGuardianClient-Service/Admin
Microsoft-Windows-HostGuardianClient-Service/Operational
Microsoft-Windows-HostGuardianService-CA/Admin
Microsoft-Windows-HostGuardianService-CA/Operational
Microsoft-Windows-HostGuardianService-Client/Admin
Microsoft-Windows-HostGuardianService-Client/Operational
Microsoft-Windows-HotspotAuth/Operational
Microsoft-Windows-HttpService/Log
Microsoft-Windows-HttpService/Trace
Microsoft-Windows-IdCtrls/Operational
Microsoft-Windows-International/Operational
Microsoft-Windows-International-RegionalOptionsControlPanel/Operational
Microsoft-Windows-Iphlpsvc/Operational
Microsoft-Windows-IPxlatCfg/Operational
Microsoft-Windows-Kernel-ApphelpCache/Operational
Microsoft-Windows-Known Folders API Service
Microsoft-Windows-LinkLayerDiscoveryProtocol/Operational
Microsoft-Windows-MediaFoundation-Performance/SARStreamResource
Microsoft-Windows-Mobile-Broadband-Experience-Parser-Task/Operational
Microsoft-Windows-Mobile-Broadband-Experience-SmsRouter/Admin
Microsoft-Windows-ModernDeployment-Diagnostics-Provider/Admin
Microsoft-Windows-ModernDeployment-Diagnostics-Provider/Autopilot
Microsoft-Windows-ModernDeployment-Diagnostics-Provider/ManagementService
Microsoft-Windows-Mprddm/Operational
Microsoft-Windows-MSPaint/Admin
Microsoft-Windows-Ncasvc/Operational
Microsoft-Windows-NcdAutoSetup/Operational
Microsoft-Windows-NCSI/Operational
Microsoft-Windows-NDIS/Operational
Microsoft-Windows-NetworkLocationWizard/Operational
Microsoft-Windows-NetworkProfile/Operational
Microsoft-Windows-NetworkProvisioning/Operational
Microsoft-Windows-NlaSvc/Operational
Microsoft-Windows-OfflineFiles/Operational
Microsoft-Windows-OneBackup/Debug
Microsoft-Windows-OneX/Operational
Microsoft-Windows-OOBE-Machine-DUI/Operational
Microsoft-Windows-OtpCredentialProvider/Operational
Microsoft-Windows-PackageStateRoaming/Operational
Microsoft-Windows-PerceptionRuntime/Operational
Microsoft-Windows-PerceptionSensorDataService/Operational
Microsoft-WindowsPhone-Connectivity-WiFiConnSvc-Channel
Microsoft-Windows-PowerShell/Admin
Microsoft-Windows-PowerShell/Operational
Microsoft-Windows-PowerShell-DesiredStateConfiguration-FileDownloadManager/Operational
Microsoft-Windows-PrintBRM/Admin
Microsoft-Windows-PrintService/Admin
Microsoft-Windows-PrintService/Operational
Microsoft-Windows-PriResources-Deployment/Operational
Microsoft-Windows-Provisioning-Diagnostics-Provider/Admin
Microsoft-Windows-Provisioning-Diagnostics-Provider/AutoPilot
Microsoft-Windows-Provisioning-Diagnostics-Provider/ManagementService
Microsoft-Windows-Proximity-Common/Diagnostic
Microsoft-Windows-PushNotification-Platform/Admin
Microsoft-Windows-PushNotification-Platform/Operational
Microsoft-Windows-RasAgileVpn/Operational
Microsoft-Windows-ReadyBoost/Operational
Microsoft-Windows-Regsvr32/Operational
Microsoft-Windows-RemoteApp and Desktop Connections/Admin
Microsoft-Windows-RemoteApp and Desktop Connections/Operational
Microsoft-Windows-RemoteAssistance/Admin
Microsoft-Windows-RemoteAssistance/Operational
Microsoft-Windows-RemoteDesktopServices-RdpCoreTS/Admin
Microsoft-Windows-RemoteDesktopServices-RdpCoreTS/Operational
Microsoft-Windows-RemoteDesktopServices-RemoteFX-Manager/Admin
Microsoft-Windows-RemoteDesktopServices-RemoteFX-Manager/Operational
Microsoft-Windows-RemoteDesktopServices-SessionServices/Operational
Microsoft-Windows-Remotefs-Rdbss/Operational
Microsoft-Windows-Resource-Exhaustion-Resolver/Operational
Microsoft-Windows-RestartManager/Operational
Microsoft-Windows-RetailDemo/Admin
Microsoft-Windows-RetailDemo/Operational
Microsoft-Windows-RRAS/Operational
Microsoft-Windows-SearchUI/Operational
Microsoft-Windows-SecureAssessment/Operational
Microsoft-Windows-Security-Audit-Configuration-Client/Operational
Microsoft-Windows-Security-EnterpriseData-FileRevocationManager/Operational
Microsoft-Windows-Security-ExchangeActiveSyncProvisioning/Operational
Microsoft-Windows-Security-IdentityListener/Operational
Microsoft-Windows-Security-Mitigations/UserMode
Microsoft-Windows-SecurityMitigationsBroker/Admin
Microsoft-Windows-SecurityMitigationsBroker/Operational
Microsoft-Windows-Security-SPP-UX-GenuineCenter-Logging/Operational
Microsoft-Windows-Security-SPP-UX-Notifications/ActionCenter
Microsoft-Windows-SENSE/Operational
Microsoft-Windows-SenseIR/Operational
Microsoft-Windows-SettingSync/Debug
Microsoft-Windows-SettingSync/Operational
Microsoft-Windows-SettingSync-Azure/Debug
Microsoft-Windows-SettingSync-Azure/Operational
Microsoft-Windows-SettingSync-OneDrive/Debug
Microsoft-Windows-SettingSync-OneDrive/Operational
Microsoft-Windows-ShellCommon-StartLayoutPopulation/Operational
Microsoft-Windows-Shell-ConnectedAccountState/ActionCenter
Microsoft-Windows-Shell-Core/ActionCenter
Microsoft-Windows-Shell-Core/AppDefaults
Microsoft-Windows-Shell-Core/LogonTasksChannel
Microsoft-Windows-Shell-Core/Operational
Microsoft-Windows-SmartCard-Audit/Authentication
Microsoft-Windows-SmartCard-DeviceEnum/Operational
Microsoft-Windows-SmartScreen/Debug
Microsoft-Windows-SMBWitnessClient/Admin
Microsoft-Windows-SMBWitnessClient/Informational
Microsoft-Windows-StateRepository/Operational
Microsoft-Windows-StorageManagement/Operational
Microsoft-Windows-StorageSpaces-ManagementAgent/WHC
Microsoft-Windows-StorageSpaces-SpaceManager/Diagnostic
Microsoft-Windows-StorageSpaces-SpaceManager/Operational
Microsoft-Windows-Storage-Tiering/Admin
Microsoft-Windows-Store/Operational
Microsoft-Windows-SystemSettingsThreshold/Operational
Microsoft-Windows-TaskScheduler/Maintenance
Microsoft-Windows-TaskScheduler/Operational
Microsoft-Windows-TerminalServices-ClientUSBDevices/Admin
Microsoft-Windows-TerminalServices-ClientUSBDevices/Operational
Microsoft-Windows-TerminalServices-LocalSessionManager/Admin
Microsoft-Windows-TerminalServices-LocalSessionManager/Operational
Microsoft-Windows-TerminalServices-PnPDevices/Admin
Microsoft-Windows-TerminalServices-PnPDevices/Operational
Microsoft-Windows-TerminalServices-Printers/Admin
Microsoft-Windows-TerminalServices-Printers/Operational
Microsoft-Windows-TerminalServices-RDPClient/Operational
Microsoft-Windows-TerminalServices-RemoteConnectionManager/Admin
Microsoft-Windows-TerminalServices-RemoteConnectionManager/Operational
Microsoft-Windows-TerminalServices-ServerUSBDevices/Admin
Microsoft-Windows-TerminalServices-ServerUSBDevices/Operational
Microsoft-Windows-Time-Service/Operational
Microsoft-Windows-Time-Service-PTP-Provider/PTP-Operational
Microsoft-Windows-Troubleshooting-Recommended/Admin
Microsoft-Windows-Troubleshooting-Recommended/Operational
Microsoft-Windows-TWinUI/Operational
Microsoft-Windows-TZSync/Operational
Microsoft-Windows-TZUtil/Operational
Microsoft-Windows-UAC/Operational
Microsoft-Windows-UniversalTelemetryClient/Operational
Microsoft-Windows-User Control Panel/Operational
Microsoft-Windows-User Device Registration/Admin
Microsoft-Windows-User Profile Service/Operational
Microsoft-Windows-User-Loader/Operational
Microsoft-Windows-UserPnp/ActionCenter
Microsoft-Windows-UserPnp/DeviceInstall
Microsoft-Windows-VerifyHardwareSecurity/Admin
Microsoft-Windows-VerifyHardwareSecurity/Operational
Microsoft-Windows-VPN-Client/Operational
Microsoft-Windows-Wcmsvc/Operational
Microsoft-Windows-WDAG-PolicyEvaluator-CSP/Operational
Microsoft-Windows-WDAG-PolicyEvaluator-GP/Operational
Microsoft-Windows-WDAG-Service/Operational
Microsoft-Windows-WebAuth/Operational
Microsoft-Windows-WebAuthN/Operational
Microsoft-Windows-WebIO-NDF/Diagnostic
Microsoft-Windows-WEPHOSTSVC/Operational
Microsoft-Windows-WER-PayloadHealth/Operational
Microsoft-Windows-Windows Firewall With Advanced Security/Firewall
Microsoft-Windows-Windows Firewall With Advanced Security/FirewallDiagnostics
Microsoft-Windows-Windows Firewall With Advanced Security/FirewallVerbose
Microsoft-Windows-WindowsColorSystem/Operational
Microsoft-Windows-WindowsSystemAssessmentTool/Operational
Microsoft-Windows-WindowsUIImmersive/Operational
Microsoft-Windows-WinHTTP-NDF/Diagnostic
Microsoft-Windows-WinINet-Capture/Analytic
Microsoft-Windows-WinINet-Config/ProxyConfigChanged
Microsoft-Windows-Winlogon/Operational
Microsoft-Windows-WinRM/Operational
Microsoft-Windows-Winsock-NameResolution/Operational
Microsoft-Windows-Wired-AutoConfig/Operational
Microsoft-Windows-WLAN-AutoConfig/Operational
Microsoft-Windows-WMI-Activity/Operational
Microsoft-Windows-WMPNSS-Service/Operational
Microsoft-Windows-Wordpad/Admin
Microsoft-Windows-WorkFolders/Operational
Microsoft-Windows-WorkFolders/WHC
Microsoft-Windows-Workplace Join/Admin
Microsoft-Windows-WWAN-SVC-Events/Operational
OpenSSH/Admin
OpenSSH/Operational
RemoteDesktopServices-RemoteFX-SessionLicensing-Admin
RemoteDesktopServices-RemoteFX-SessionLicensing-Operational
Setup
SMSApi
Windows PowerShell
8.2、附录B:受安全对象支持的 SACL 审核消息
上面提到,msobjs.dll 中包含的字符串可以提供一些有价值的见解,以了解哪些安全对象支持 SACL 审核。我提取了所有受支持的消息,并根据以下列表中的安全对象将它们进行分组。希望会激起你对所在环境中应用目标 SACL的兴趣,以补充你的整体检测情况。
ALPC Port:
Communicate using port
Channel:
Channel read message
Channel write message
Channel query information
Channel set information
Desktop:
Read Objects
Create window
Create menu
Hook control
Journal (record)
Journal (playback)
Include this desktop in enumerations
Write objects
Switch to this desktop
Device:
Device Access Bit 0
Device Access Bit 1
Device Access Bit 2
Device Access Bit 3
Device Access Bit 4
Device Access Bit 5
Device Access Bit 6
Device Access Bit 7
Device Access Bit 8
Directory:
Query directory
Traverse
Create object in directory
Create sub-directory
Event:
Query event state
Modify event state
File, MailSlot, and NamedPipe:
ReadData (or ListDirectory)
WriteData (or AddFile)
AppendData (or AddSubdirectory or CreatePipeInstance)
ReadEA
WriteEA
Execute/Traverse
DeleteChild
ReadAttributes
WriteAttributes
IoCompletion:
Query State
Modify State
Job:
Assign process
Set Attributes
Query Attributes
Terminate Job
Set Security Attributes
Key:
Query key value
Set key value
Create sub-key
Enumerate sub-keys
Notify about changes to keys
Create Link
Undefined Access (no effect) Bit 6
Undefined Access (no effect) Bit 7
Enable 64(or 32) bit application to open 64 bit key
Enable 64(or 32) bit application to open 32 bit key
KeyedEvent:
KeyedEvent Wait
KeyedEvent Wake
Mutant:
Query mutant state
Port and WaitablePort:
Communicate using port
Process:
Force process termination
Create new thread in process
Set process session ID
Perform virtual memory operation
Read from process memory
Write to process memory
Duplicate handle into or out of process
Create a subprocess of process
Set process quotas
Set process information
Query process information
Set process termination port
Profile:
Control profile
Section:
Query section state
Map section for write
Map section for read
Map section for execute
Extend size
Semaphore:
Query semaphore state
Modify semaphore state
SymbolicLink:
Use symbolic link
Thread:
Force thread termination
Suspend or resume thread
Send an alert to thread
Get thread context
Set thread context
Set thread information
Query thread information
Assign a token to the thread
Cause thread to directly impersonate another thread
Directly impersonate this thread
Timer:
Query timer state
Modify timer state
Token:
AssignAsPrimary
Duplicate
Impersonate
Query
QuerySource
AdjustPrivileges
AdjustGroups
AdjustDefaultDacl
AdjustSessionID
Type:
Create instance of object type
WindowsStation:
Enumerate desktops
Read attributes
Access Clipboard
Create desktop
Write attributes
Access global atoms
Exit windows
Unused Access Flag
Include this windowstation in enumerations
Read screen
WMI Namespace:
Enable WMI Account
Execute Method
Full Write
Partial Write
Provider Write
Remote Access
Subscribe
Publish








发表评论
您还未登录,请先登录。
登录